Identity Management
How do you configure a Salesforce integration profile in ServiceNow?
To configure a Salesforce integration profile in ServiceNow, first create a profile with an appropriate name in the ServiceNow workspace. Then set up connection credentials by navigating to the classic interface where you'll enter the Salesforce connection URL, OAuth client ID (consumer key), OAuth client secret (consumer secret), and ServiceNow redirect URL. Once submitted, the system will validate the connection and generate authentication tokens (both access and refresh tokens) that enable data exchange between systems. These tokens allow ServiceNow to load data from Salesforce with the access token refreshing automatically when needed.
Watch clip answer (09:43m)How can I enhance the security of my LinkedIn account?
You can enhance LinkedIn security by managing several privacy settings. First, navigate to Settings and Privacy through your profile icon. Review your feed preferences to control what appears in your newsfeed and who you follow. Check permitted services to revoke access from third-party apps you no longer use, such as Buffer, Hootsuite, or Twitter. These connections might still have access to your profile information. Additionally, consider enabling two-factor authentication to protect your account from unauthorized access.
Watch clip answer (05:15m)How can we understand authentic selfhood in a dialogical context rather than as an individualistic pursuit?
According to Yale lecturer Matthew Croasmun, authentic selfhood isn't discovered in isolation but formed through dialogical relationships with significant others. He challenges the notion that we are self-standing individuals, emphasizing that our selves are historically situated and constantly being formed through community. True authenticity involves recognizing that we are interconnected beings whose identities emerge through meaningful relationships with others. Rather than projecting ourselves to the world as isolated individuals, ethical authenticity requires us to acknowledge our shared horizons of significance and engage in the work of recognition with others, which may ultimately lead us to discover our unique vocations and callings.
Watch clip answer (03:02m)How do I verify my LinkedIn account and what are the benefits?
LinkedIn verification increases profile views by up to 60%, improves message response rates, and elevates your personal brand's credibility. The process is relatively quick, requiring your mobile device and passport for identity verification. First, locate the verification option on your profile or homepage, then follow the guided steps that include scanning your passport, verifying the NFC chip, and completing facial recognition checks by looking straight, left, and right. The verification badge appears almost immediately after successful completion, distinguishing your profile as authentic.
Watch clip answer (03:04m)How are AI chatbots amplifying social engineering scams?
AI chatbots are revolutionizing social engineering scams by functioning as automated con artists that can engage multiple victims simultaneously. They maintain seemingly genuine conversations over extended periods, impersonating romantic partners, investment advisors, and tech support personnel with unprecedented efficiency. These AI systems excel at emotional manipulation through perfectly tailored responses, remembering personal details, writing love poems, and responding instantly with affection. As one cybersecurity expert explains, they make conversations sound remarkably authentic in ways impossible just years ago. The technology enables scammers to bypass human limitations, with bots handling the emotional labor while criminals focus on extracting money or personal information from victims.
Watch clip answer (07:00m)What are the essential elements of JWT authentication in API security?
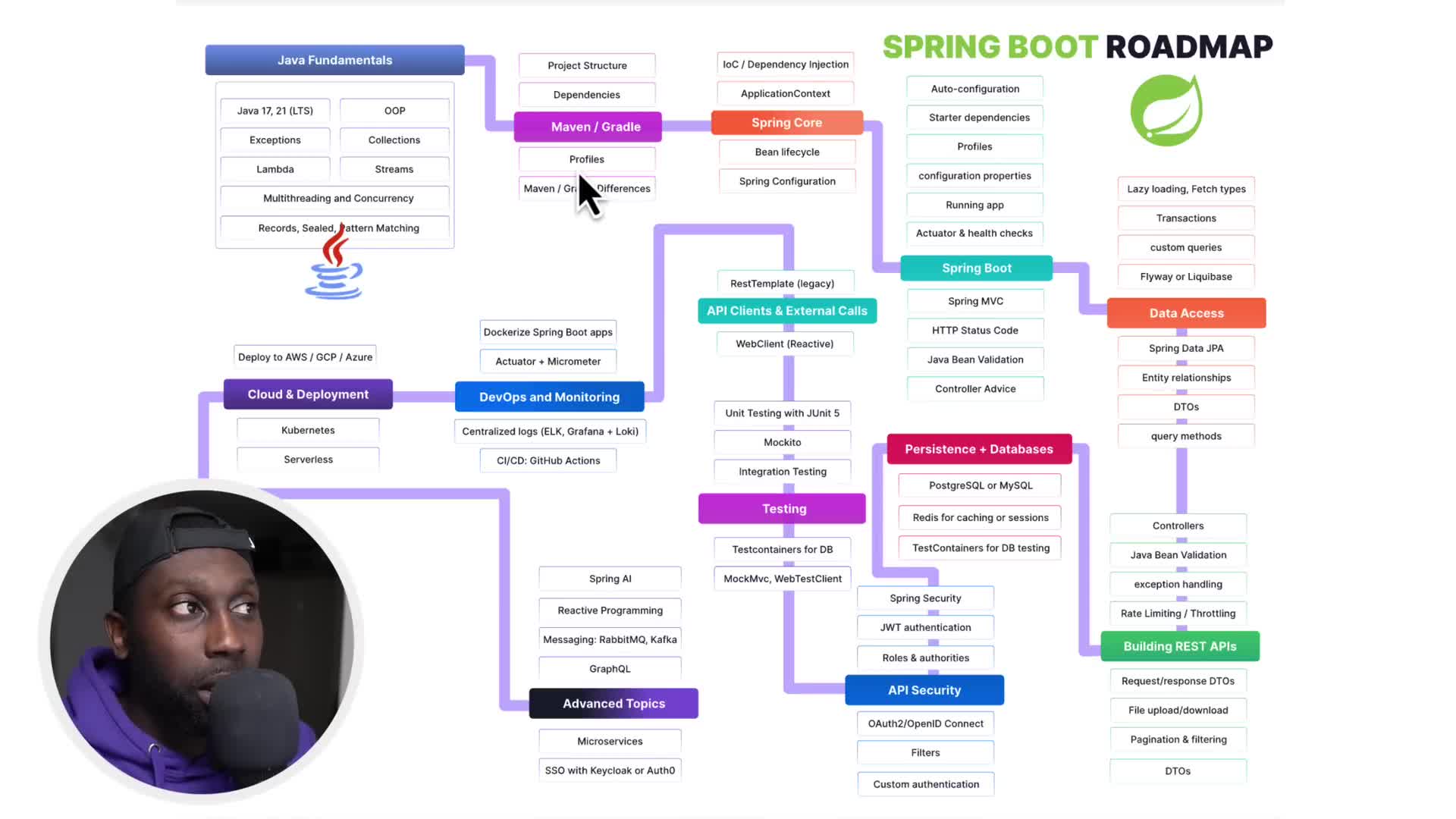
JWT (JSON Web Token) authentication is a crucial security mechanism for APIs. Developers should first understand what JWT is, then implement a simple project with login and logout functionality. It's important to incorporate roles and authentication authorities that control access to resources - like a badge that determines what actions users can perform (read-only, write-only, etc.). JWT works alongside OAuth and Open ID Connect filters to enable custom authentication methods. Security is a comprehensive topic that extends beyond basic authentication to include proper access control that protects application resources based on user permissions. This approach ensures applications remain secure while providing appropriate access levels to different users.
Watch clip answer (03:56m)