Data Security
Data security encompasses the comprehensive measures, strategies, and technologies aimed at safeguarding digital information from unauthorized access, corruption, theft, or loss throughout its entire lifecycle. As organizations increasingly rely on digital infrastructures, the prevalence of data breaches and cyber threats—such as ransomware, phishing, and insider threats—has elevated the importance of robust data security protocols. With the average cost of a data breach reaching significant heights, effective data protection is not just a regulatory obligation (as seen with GDPR, HIPAA, and PCI DSS), but also a critical component in maintaining customer trust and business integrity. The contemporary data security landscape emphasizes the need for advanced solutions, including encryption and multi-factor authentication, as well as the implementation of cybersecurity best practices that incorporate identity management, access controls, and incident response plans. As artificial intelligence continues to reshape operational landscapes, it also introduces new vulnerabilities; therefore, organizations must adopt a layered security approach to manage risks associated with both human error and sophisticated cyberattacks. Setting a solid foundation for data security means establishing protocols that ensure confidentiality, integrity, and availability of sensitive data while adapting to emerging threats and regulatory demands. By focusing on continual improvement and innovative security solutions, businesses can mitigate risks and protect valuable information assets amid evolving digital challenges.
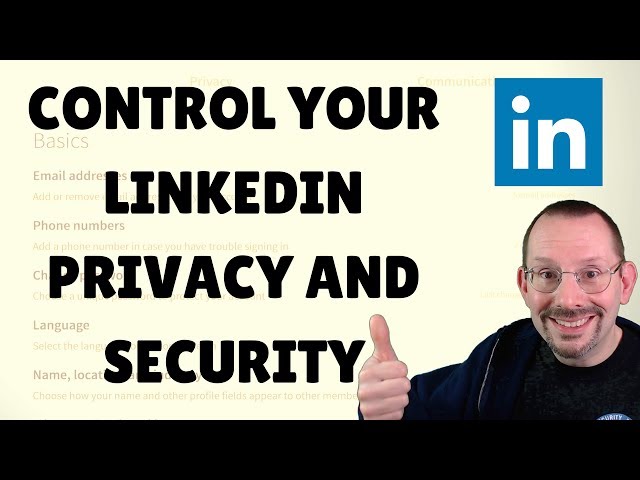
How can I enhance the security of my LinkedIn account?
You can enhance LinkedIn security by managing several privacy settings. First, navigate to Settings and Privacy through your profile icon. Review your feed preferences to control what appears in your newsfeed and who you follow. Check permitted services to revoke access from third-party apps you no longer use, such as Buffer, Hootsuite, or Twitter. These connections might still have access to your profile information. Additionally, consider enabling two-factor authentication to protect your account from unauthorized access.
Watch clip answer (05:15m)How do you measure success in technology implementations?
Success in technology implementations cannot simply be defined as avoiding breaches or hacks. While this is a common perception, it requires more comprehensive metrics. From an organizational perspective, success must be measured both at the macro level and within specific teams like development. Developers need clear indicators to know whether their efforts, time investments, and adherence to organizational directives are truly effective. Success metrics should translate into measurable program outcomes that balance security requirements with development goals and demonstrate value beyond the absence of negative events.
Watch clip answer (01:15m)What is Security Compliance?
Security compliance refers to following regulations, standards and guidelines set to protect sensitive information and data. It ensures that organizations implement necessary measures to safeguard data from unauthorized access or breaches, and is crucial in various industries to maintain data integrity and confidentiality. The process involves regular audits and assessments to ensure adherence to legal requirements and industry best practices. Non-compliance can result in severe consequences, including financial penalties and damage to an organization's reputation. By implementing proper security compliance measures, organizations demonstrate their commitment to protecting data security and privacy.
Watch clip answer (00:42m)How can I back up my LinkedIn profile to protect it from being compromised?
To back up your LinkedIn profile, click on the 'More' option and select 'Save to PDF.' This process creates a complete backup of all your profile content in PDF format, which serves as protection against account compromise. This backup is particularly valuable because if your account gets compromised, you can refer to this PDF to review all your written content, messages, and other profile information. Having this backup ensures you can restore your professional presence even if you lose access to your LinkedIn account.
Watch clip answer (00:32m)What was the prolonged hacking campaign that targeted the U.S. Treasury and critical infrastructure?
The U.S. experienced a prolonged hacking campaign that targeted the Treasury and other critical infrastructure from August 2013 to December 2024. The campaign, which lasted more than 11 years, was conducted by two Chinese hackers who were recently indicted by the Department of Justice. These hackers caused millions of dollars in damages by targeting government agencies, private companies, and non-profit organizations across the United States. Additionally, Chinese companies involved in covering up the illegal hacking activities have also been sanctioned by the U.S. government.
Watch clip answer (07:46m)What happens when organizations fail to implement cybersecurity recommendations after a breach?
As illustrated by Lee Kim's client example, organizations that experience a breach but fail to improve their cybersecurity measures often face repeated attacks. This particular client suffered a second breach just two weeks after the initial incident because they neglected to conduct a postmortem analysis, implement tabletop exercises to test defenses, or deploy necessary security tools. In healthcare especially, the stakes are exceptionally high since compromised patient data, unlike financial information, cannot be replaced or restored once exposed. Breached healthcare data, particularly sensitive information like genomic sequences, remains permanently vulnerable once compromised.
Watch clip answer (00:55m)