Data Security
Data security encompasses the comprehensive measures, strategies, and technologies aimed at safeguarding digital information from unauthorized access, corruption, theft, or loss throughout its entire lifecycle. As organizations increasingly rely on digital infrastructures, the prevalence of data breaches and cyber threats—such as ransomware, phishing, and insider threats—has elevated the importance of robust data security protocols. With the average cost of a data breach reaching significant heights, effective data protection is not just a regulatory obligation (as seen with GDPR, HIPAA, and PCI DSS), but also a critical component in maintaining customer trust and business integrity. The contemporary data security landscape emphasizes the need for advanced solutions, including encryption and multi-factor authentication, as well as the implementation of cybersecurity best practices that incorporate identity management, access controls, and incident response plans. As artificial intelligence continues to reshape operational landscapes, it also introduces new vulnerabilities; therefore, organizations must adopt a layered security approach to manage risks associated with both human error and sophisticated cyberattacks. Setting a solid foundation for data security means establishing protocols that ensure confidentiality, integrity, and availability of sensitive data while adapting to emerging threats and regulatory demands. By focusing on continual improvement and innovative security solutions, businesses can mitigate risks and protect valuable information assets amid evolving digital challenges.
What critical security failures did the FTC identify at GoDaddy that led to multiple breaches?
The FTC identified several fundamental security lapses at GoDaddy that contributed to multiple breaches between 2019-2022. Most notably, GoDaddy lacked basic multifactor authentication (MFA) for critical systems, which allowed attackers to gain access through a single compromised password in one incident that exposed 1.2 million WordPress customers' data. Other significant failures included improper software update management, insufficient security event logging, lack of network segmentation, poor asset tracking, and inadequate monitoring for threats. These gaps enabled attackers to install malware, steal source code, and access sensitive customer information including email addresses, admin passwords, database logins, and even SSL private keys - essentially providing complete access to websites and their data.
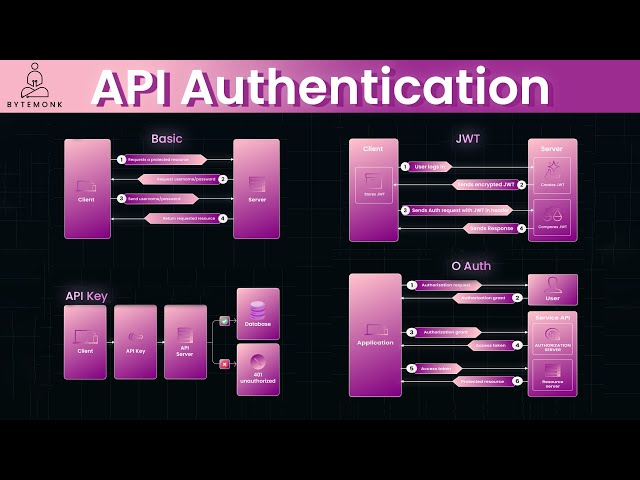
Watch clip answer (03:18m)What is JWT authentication and how does it work?
JWT (JSON Web Token) is a compact, stateless mechanism for API authentication. When a user logs in, the API server creates a digitally signed, encrypted token containing the user's identity. The client includes this JWT in every subsequent request for validation. The user's data isn't stored server-side, improving scalability. JWT is popular because it allows servers to issue tokens that clients use for future authentication without storing session data. The token contains signed user information that can't be tampered with, making it ideal for securing APIs in stateless environments.
Watch clip answer (01:34m)How has Reddit's stance on AI companies been hypocritical?
Reddit has positioned itself as a victim of AI companies, claiming these companies scrape content without permission, while simultaneously negotiating massive licensing deals and selling users' posts, comments, and metadata to corporations like OpenAI for model training without user consent or transparency. This hypocrisy reveals that Reddit's outrage isn't about ethics or protecting their community, but about losing control over who profits from user data exploitation. While publicly criticizing AI companies, Reddit executives have willingly turned the platform into a commercial data farm when it served their financial interests, betraying their self-portrayal as defenders of privacy.
Watch clip answer (08:25m)How has cybercrime changed during the pandemic?
During the pandemic, cybercrime has increased disproportionately compared to pre-2019 levels. This significant rise is attributed to inadequate home security systems and organizations lacking proper secure architecture like firewalls. According to experts, the number of digital misdemeanor events and the quantum of losses have substantially increased as people worked remotely. Many victims fell prey to these crimes due to negligence, mistakes, or simply being targets of wrongdoing, highlighting how the pandemic exposed critical vulnerabilities in existing cybersecurity infrastructures.
Watch clip answer (01:33m)What led to the resignations of top officials at government agencies and how did the courts respond to challenges against Musk's data access?
Top officials at the Social Security Administration and Treasury Department resigned after Elon Musk's staff demanded access to sensitive information about millions of Americans. When challenged legally, a federal judge refused to immediately block Musk's team from accessing government data systems, stating that while there are legitimate questions about the unchecked authority of an unelected individual, the states who sued failed to demonstrate irreparable harm. The situation has raised significant concerns among Democrats and critics who argue there is insufficient oversight of this access to sensitive government data. The judge's ruling highlights the tension between government efficiency initiatives and the protection of sensitive information when private sector figures are granted access to federal data systems.
Watch clip answer (00:29m)What are the key recommendations for creating secure passwords?
According to Hostn IT Service Management, users should avoid common password setups like '123456' or simply 'password' as these are easily hackable. Instead, create long, complex passwords that combine uppercase and lowercase letters, numbers, and special characters to significantly enhance online security. Additionally, it's crucial to avoid reusing passwords across multiple sites, as a breach on one platform can compromise all your accounts. Implementing these password management practices helps protect both personal and professional data from unauthorized access in today's digital landscape.
Watch clip answer (00:03m)