Data Protection
Data protection is an essential concept in today’s digital landscape, encompassing strategies aimed at safeguarding sensitive data from unauthorized access, loss, or corruption. This multi-faceted discipline includes a range of practices and technologies, such as data encryption, backup solutions, and incident response plans, which ensure data integrity, availability, and compliance with various legal requirements. With tightening global regulations like the General Data Protection Regulation (GDPR) in Europe and the California Consumer Privacy Act (CCPA) in the United States, organizations are increasingly prioritizing robust data protection frameworks to avoid heavy penalties and maintain customer trust. The relevance of data protection is underscored by alarming statistics revealing that the average cost of a data breach reached millions, highlighting the financial and reputational stakes involved. Modern data protection practices not only focus on preventing breaches but also emphasize the importance of data management throughout its lifecycle—from collection to destruction—while ensuring compliance with evolving data privacy laws. As regulatory environments become more stringent and consumers demand increased transparency and control over their personal information, adopting effective data protection measures is no longer optional for organizations; it is a critical business necessity. In this context, understanding key elements of data privacy laws, such as data minimization and user consent requirements, as well as the tools and technologies that facilitate compliance is crucial for organizations operating in an increasingly complex and data-driven world.
How can I enhance the security of my LinkedIn account?
You can enhance LinkedIn security by managing several privacy settings. First, navigate to Settings and Privacy through your profile icon. Review your feed preferences to control what appears in your newsfeed and who you follow. Check permitted services to revoke access from third-party apps you no longer use, such as Buffer, Hootsuite, or Twitter. These connections might still have access to your profile information. Additionally, consider enabling two-factor authentication to protect your account from unauthorized access.
Watch clip answer (05:15m)What is Security Compliance?
Security compliance refers to following regulations, standards and guidelines set to protect sensitive information and data. It ensures that organizations implement necessary measures to safeguard data from unauthorized access or breaches, and is crucial in various industries to maintain data integrity and confidentiality. The process involves regular audits and assessments to ensure adherence to legal requirements and industry best practices. Non-compliance can result in severe consequences, including financial penalties and damage to an organization's reputation. By implementing proper security compliance measures, organizations demonstrate their commitment to protecting data security and privacy.
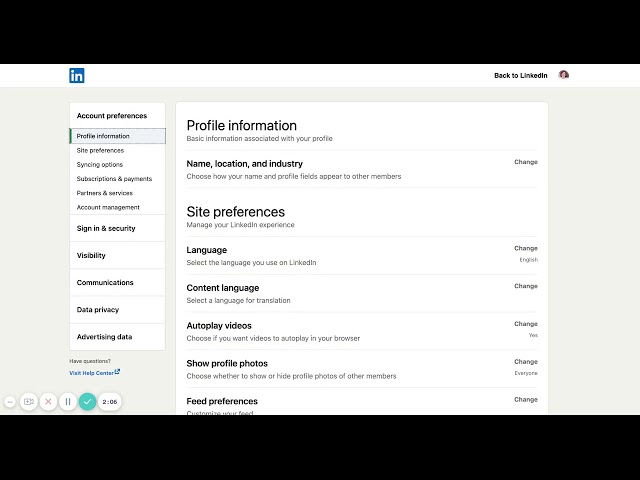
Watch clip answer (00:42m)What are the key LinkedIn privacy settings users should adjust to protect their profile?
Three essential LinkedIn privacy settings can enhance profile protection. First, users should consider turning off notifications for profile updates such as job changes and work anniversaries when making routine updates, enabling them only for significant announcements. Second, limiting who can see your connections list protects your professional network—change this from the default 'all connections' to 'only you' to safeguard your valuable business database. Third, adjust profile viewing options to control your visibility when browsing others' profiles, using anonymous mode when researching competitors to avoid leaving digital footprints.
Watch clip answer (04:27m)How can I back up my LinkedIn profile to protect it from being compromised?
To back up your LinkedIn profile, click on the 'More' option and select 'Save to PDF.' This process creates a complete backup of all your profile content in PDF format, which serves as protection against account compromise. This backup is particularly valuable because if your account gets compromised, you can refer to this PDF to review all your written content, messages, and other profile information. Having this backup ensures you can restore your professional presence even if you lose access to your LinkedIn account.
Watch clip answer (00:32m)What happens when organizations fail to implement cybersecurity recommendations after a breach?
As illustrated by Lee Kim's client example, organizations that experience a breach but fail to improve their cybersecurity measures often face repeated attacks. This particular client suffered a second breach just two weeks after the initial incident because they neglected to conduct a postmortem analysis, implement tabletop exercises to test defenses, or deploy necessary security tools. In healthcare especially, the stakes are exceptionally high since compromised patient data, unlike financial information, cannot be replaced or restored once exposed. Breached healthcare data, particularly sensitive information like genomic sequences, remains permanently vulnerable once compromised.
Watch clip answer (00:55m)What critical security failures did the FTC identify at GoDaddy that led to multiple breaches?
The FTC identified several fundamental security lapses at GoDaddy that contributed to multiple breaches between 2019-2022. Most notably, GoDaddy lacked basic multifactor authentication (MFA) for critical systems, which allowed attackers to gain access through a single compromised password in one incident that exposed 1.2 million WordPress customers' data. Other significant failures included improper software update management, insufficient security event logging, lack of network segmentation, poor asset tracking, and inadequate monitoring for threats. These gaps enabled attackers to install malware, steal source code, and access sensitive customer information including email addresses, admin passwords, database logins, and even SSL private keys - essentially providing complete access to websites and their data.
Watch clip answer (03:18m)