Data Privacy
Data privacy refers to the proper handling, storage, and usage of sensitive personal information to safeguard individuals' privacy rights and ensure compliance with regulatory requirements. As organizations increasingly collect personally identifiable information (PII), protected health information (PHI), and financial data, the need for robust data privacy practices has become paramount. Effective data privacy not only promotes transparency and informed consent but also protects against data breaches that can lead to identity theft and fraud. With the rise of innovative technologies and heightened consumer awareness, the ethical governance of data practices has taken center stage. Recently, the landscape of data privacy law has transformed significantly, especially in the United States, where numerous state privacy laws have been enacted. By 2025, various states have introduced comprehensive privacy regulations, reflecting a growing trend towards strict consumer data protections and enforcement mechanisms. Key laws such as the California Consumer Privacy Act (CCPA) and various state statutes emphasize universal opt-out options and stringent regulations on data collection and sharing. This evolving regulatory environment demands that organizations implement multifaceted compliance strategies that adapt to differing state laws. As organizations navigate these challenges, effective privacy compliance software has become essential for managing their obligations while respecting the rights of individuals. These developments underscore the importance of data privacy not just as a legal requirement but as a competitive advantage in the digital marketplace. Businesses that prioritize data protection and compliance are likely to gain consumer trust, leading to better customer relationships and enhanced business reputation in an era where data is increasingly viewed as a vital asset.
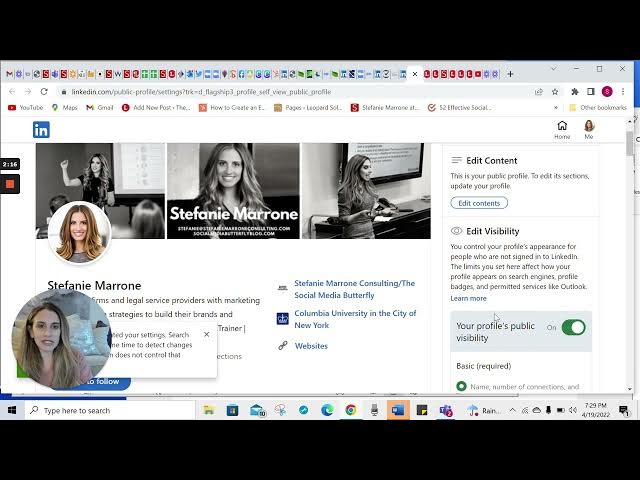
How can I control what people see on my LinkedIn profile?
LinkedIn offers comprehensive visibility settings that allow you to control what others see when viewing your profile. You can edit visibility by accessing profile settings where you'll find options to show your profile photo to everyone, only LinkedIn members, or just first-degree connections. For each profile section (work experience, education), you can toggle switches to determine whether details are visible to the public. While you have control over privacy, Stephanie Marone recommends maintaining visibility since LinkedIn's purpose is to be visible online. Basic information is required, but you can choose which specific details to share. This flexibility enables you to present a professional image while maintaining your preferred level of privacy.
Watch clip answer (01:56m)What was the prolonged hacking campaign that targeted the U.S. Treasury and critical infrastructure?
The U.S. experienced a prolonged hacking campaign that targeted the Treasury and other critical infrastructure from August 2013 to December 2024. The campaign, which lasted more than 11 years, was conducted by two Chinese hackers who were recently indicted by the Department of Justice. These hackers caused millions of dollars in damages by targeting government agencies, private companies, and non-profit organizations across the United States. Additionally, Chinese companies involved in covering up the illegal hacking activities have also been sanctioned by the U.S. government.
Watch clip answer (07:46m)What happens when organizations fail to implement cybersecurity recommendations after a breach?
As illustrated by Lee Kim's client example, organizations that experience a breach but fail to improve their cybersecurity measures often face repeated attacks. This particular client suffered a second breach just two weeks after the initial incident because they neglected to conduct a postmortem analysis, implement tabletop exercises to test defenses, or deploy necessary security tools. In healthcare especially, the stakes are exceptionally high since compromised patient data, unlike financial information, cannot be replaced or restored once exposed. Breached healthcare data, particularly sensitive information like genomic sequences, remains permanently vulnerable once compromised.
Watch clip answer (00:55m)What are the ethical implications of AI surveillance by 2025?
By 2025, AI surveillance systems will be deployed globally by governments and corporations, raising significant ethical questions about privacy and civil liberties. These sophisticated systems enable predictive policing and real-time tracking of individuals across vast areas, with China already implementing large-scale AI surveillance networks while other countries explore similar technologies. While AI surveillance can enhance security, its potential for misuse has sparked global debates about regulation and privacy rights. As these systems continue to expand, public discourse will increasingly focus on balancing safety with individual freedoms, making AI surveillance one of the most critical and controversial technological issues facing society.
Watch clip answer (00:54m)How has Reddit's stance on AI companies been hypocritical?
Reddit has positioned itself as a victim of AI companies, claiming these companies scrape content without permission, while simultaneously negotiating massive licensing deals and selling users' posts, comments, and metadata to corporations like OpenAI for model training without user consent or transparency. This hypocrisy reveals that Reddit's outrage isn't about ethics or protecting their community, but about losing control over who profits from user data exploitation. While publicly criticizing AI companies, Reddit executives have willingly turned the platform into a commercial data farm when it served their financial interests, betraying their self-portrayal as defenders of privacy.
Watch clip answer (08:25m)What are the key recommendations for creating secure passwords?
According to Hostn IT Service Management, users should avoid common password setups like '123456' or simply 'password' as these are easily hackable. Instead, create long, complex passwords that combine uppercase and lowercase letters, numbers, and special characters to significantly enhance online security. Additionally, it's crucial to avoid reusing passwords across multiple sites, as a breach on one platform can compromise all your accounts. Implementing these password management practices helps protect both personal and professional data from unauthorized access in today's digital landscape.
Watch clip answer (00:03m)