Data Privacy
Data privacy refers to the proper handling, storage, and usage of sensitive personal information to safeguard individuals' privacy rights and ensure compliance with regulatory requirements. As organizations increasingly collect personally identifiable information (PII), protected health information (PHI), and financial data, the need for robust data privacy practices has become paramount. Effective data privacy not only promotes transparency and informed consent but also protects against data breaches that can lead to identity theft and fraud. With the rise of innovative technologies and heightened consumer awareness, the ethical governance of data practices has taken center stage. Recently, the landscape of data privacy law has transformed significantly, especially in the United States, where numerous state privacy laws have been enacted. By 2025, various states have introduced comprehensive privacy regulations, reflecting a growing trend towards strict consumer data protections and enforcement mechanisms. Key laws such as the California Consumer Privacy Act (CCPA) and various state statutes emphasize universal opt-out options and stringent regulations on data collection and sharing. This evolving regulatory environment demands that organizations implement multifaceted compliance strategies that adapt to differing state laws. As organizations navigate these challenges, effective privacy compliance software has become essential for managing their obligations while respecting the rights of individuals. These developments underscore the importance of data privacy not just as a legal requirement but as a competitive advantage in the digital marketplace. Businesses that prioritize data protection and compliance are likely to gain consumer trust, leading to better customer relationships and enhanced business reputation in an era where data is increasingly viewed as a vital asset.
What are the most hackable passwords according to recent findings?
According to a report released by Hostn IT Service Management company, many common passwords are extremely vulnerable to hacking. The report analyzes passwords based on how frequently they appear in data breaches, revealing which ones are most likely to be compromised. The analysis suggests that simple passwords like '123456' and 'password' (inferred from context) are among the most hackable options that users should avoid. The report emphasizes the importance of reevaluating password strength, as many people mistakenly believe their passwords are secure when they're actually easily compromised.
Watch clip answer (00:12m)How does one ensure that their password is safe and secure?
To ensure password safety, use complex passwords that are at least 20 characters long with a mix of uppercase and lowercase letters, numbers, and special symbols. This combination makes passwords significantly harder for hackers to crack through automated methods. Equally important is avoiding password reuse across multiple websites or services. When one account gets compromised, using the same password elsewhere puts all your other accounts at risk. Each unique service should have its own distinct password to maintain your overall digital security.
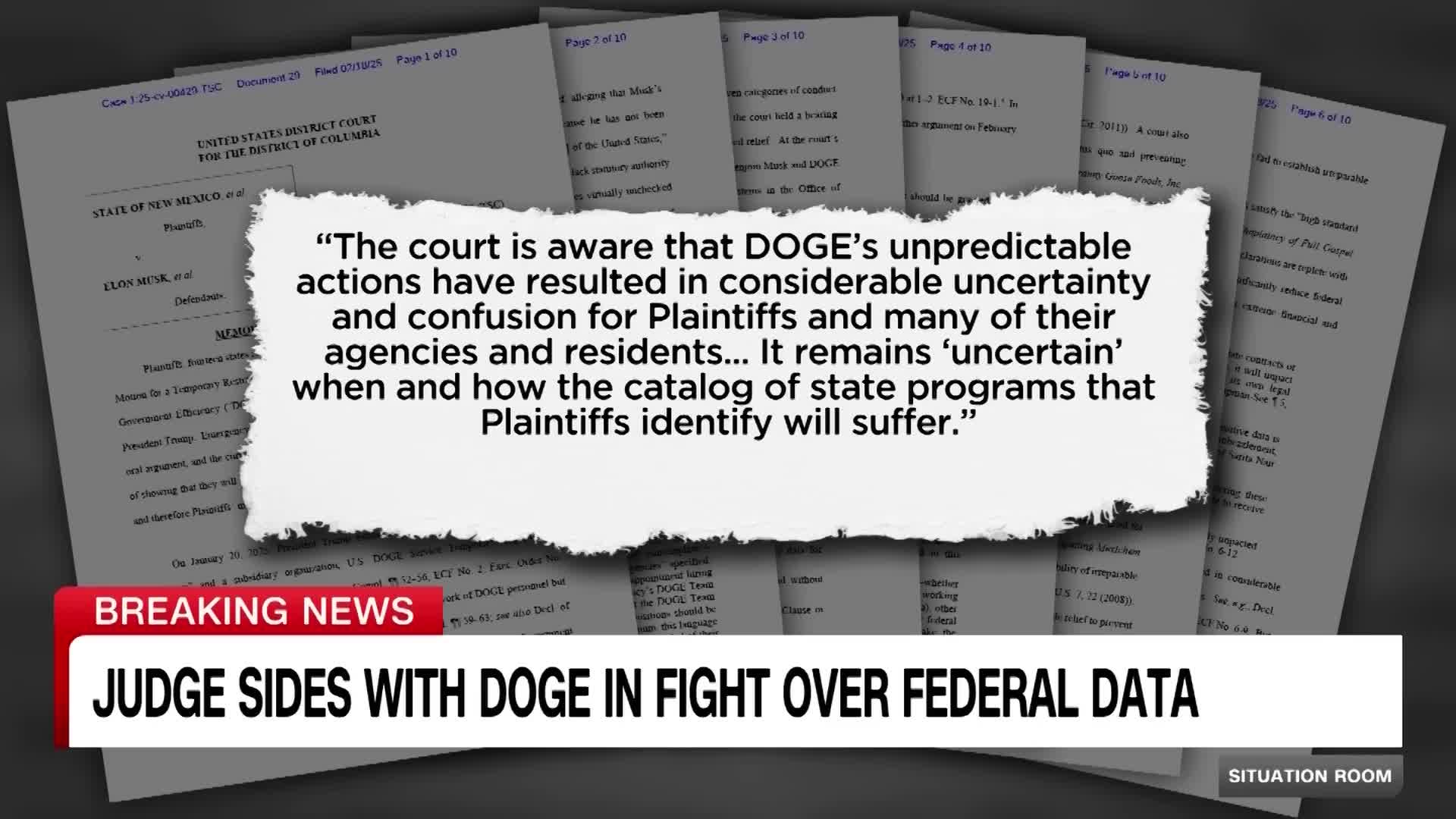
Watch clip answer (00:24m)What legal victory did the Trump administration achieve regarding Elon Musk's access to federal data?
The Trump administration scored a significant court victory when a judge rejected motions from Democratic-led ('blue') states attempting to block Elon Musk and the Department of Government Efficiency (DOGE) from accessing federal data. Judge Tanya Chutkan denied the efforts of state attorneys general who sought to restrict Musk's ability to obtain government information through his role with DOGE. This ruling represents an important win for the administration's government efficiency initiatives, allowing Musk's controversial involvement in federal data access to continue despite opposition from Democratic states.
Watch clip answer (00:16m)How does Donald Trump characterize Elon Musk in relation to his work with Doge?
Trump describes Elon Musk as a 'patriot' in relation to his work with the Department of Government Efficiency (Doge). When asked about Musk's role with Doge, Trump emphasized his view of Musk's character rather than his specific job title, stating 'you could call him an employee, you could call him a consultant, you could call him whatever you want, but he's a patriot.' This characterization highlights Trump's positive regard for Musk's involvement in the government efficiency initiative, framing his contribution as one motivated by patriotism rather than focusing on his formal position.
Watch clip answer (00:15m)What is Elon Musk's role in the Department of Government Efficiency (Doge) and why does he need access to data?
Elon Musk and his team serve as advisors to government agencies and the administration, specifically focusing on identifying fraud, waste, and abuse within the system. Their advisory role is essential for pinpointing where government inefficiencies exist and recommending improvements. To effectively fulfill this function, they sometimes require access to data, including sensitive information like Social Security numbers. This access is necessary to ensure there are no duplicates or fraudulent activities occurring within government systems. Despite concerns about privacy, their data access is purposeful - aimed at improving government efficiency through targeted analysis of where wasteful spending occurs.
Watch clip answer (00:12m)What is the relationship between accessing sensitive government information and reducing government waste?
According to the speaker, there is no legitimate connection between accessing sensitive government information and reducing government waste. The speaker rhetorically questions what sensitive information access has to do with cutting government waste or the price of eggs in Iowa, answering with "Absolutely nothing." The speaker characterizes the situation as "the fox is in the hen house," suggesting Elon Musk has been given inappropriate access without proper oversight. They criticize the Trump administration for failing to provide transparency about what information is being accessed, who is accessing it, and for what purpose. The speaker concludes that Trump appears to be unduly influenced by Musk, who has been given carte blanche to do whatever he wants.
Watch clip answer (00:33m)