Security Awareness
What is Security Compliance?
Security compliance refers to following regulations, standards and guidelines set to protect sensitive information and data. It ensures that organizations implement necessary measures to safeguard data from unauthorized access or breaches, and is crucial in various industries to maintain data integrity and confidentiality. The process involves regular audits and assessments to ensure adherence to legal requirements and industry best practices. Non-compliance can result in severe consequences, including financial penalties and damage to an organization's reputation. By implementing proper security compliance measures, organizations demonstrate their commitment to protecting data security and privacy.
Watch clip answer (00:42m)What happens when organizations fail to implement cybersecurity recommendations after a breach?
As illustrated by Lee Kim's client example, organizations that experience a breach but fail to improve their cybersecurity measures often face repeated attacks. This particular client suffered a second breach just two weeks after the initial incident because they neglected to conduct a postmortem analysis, implement tabletop exercises to test defenses, or deploy necessary security tools. In healthcare especially, the stakes are exceptionally high since compromised patient data, unlike financial information, cannot be replaced or restored once exposed. Breached healthcare data, particularly sensitive information like genomic sequences, remains permanently vulnerable once compromised.
Watch clip answer (00:55m)How does AI impact cybersecurity?
AI is a double-edged sword in cybersecurity. On one hand, it empowers defenders with advanced tools that analyze massive datasets at unprecedented speeds, detect threats in real time, identify malicious code with high accuracy, and automate incident response for more efficient handling of potential threats. This allows security teams to be more proactive rather than reactive. On the other hand, AI is also a powerful tool for attackers, enabling them to create sophisticated malware capable of adapting and evolving to bypass security measures. AI-powered attacks can generate convincing phishing attempts that trick even cautious individuals and spread disinformation at alarming rates. This dual nature makes AI both revolutionary for defense while simultaneously creating new vulnerabilities organizations must address.
Watch clip answer (01:44m)What are the key recommendations for creating secure passwords?
According to Hostn IT Service Management, users should avoid common password setups like '123456' or simply 'password' as these are easily hackable. Instead, create long, complex passwords that combine uppercase and lowercase letters, numbers, and special characters to significantly enhance online security. Additionally, it's crucial to avoid reusing passwords across multiple sites, as a breach on one platform can compromise all your accounts. Implementing these password management practices helps protect both personal and professional data from unauthorized access in today's digital landscape.
Watch clip answer (00:03m)How does one ensure that their password is safe and secure?
To ensure password safety, use complex passwords that are at least 20 characters long with a mix of uppercase and lowercase letters, numbers, and special symbols. This combination makes passwords significantly harder for hackers to crack through automated methods. Equally important is avoiding password reuse across multiple websites or services. When one account gets compromised, using the same password elsewhere puts all your other accounts at risk. Each unique service should have its own distinct password to maintain your overall digital security.
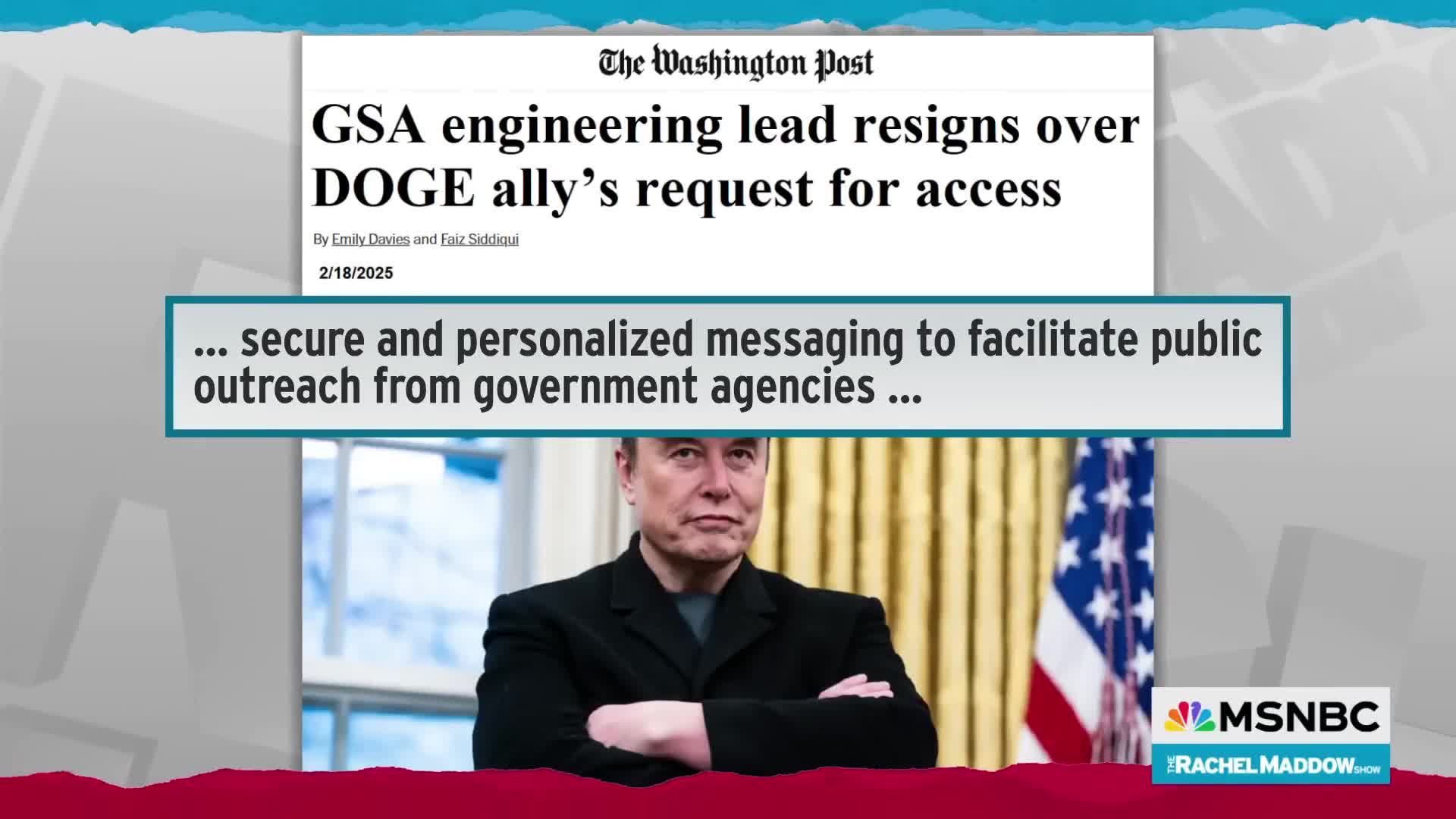
Watch clip answer (00:24m)Why did a senior engineer from the GSA resign?
A senior engineer from the General Services Administration (GSA) resigned after attempting to block one of Elon Musk's associates from accessing notify.gov, a secure government system. The engineer was concerned about privacy issues related to this sensitive platform, which connects federal agencies directly to citizens' personal cell phone numbers and information. Notify.gov contains highly sensitive data linking citizens' personal information with their involvement across multiple government agencies. The engineer took a stand against the Trump administration's effort to grant access to Musk's associate, demonstrating serious concerns about protecting Americans' personal information from potential privacy breaches.
Watch clip answer (00:44m)