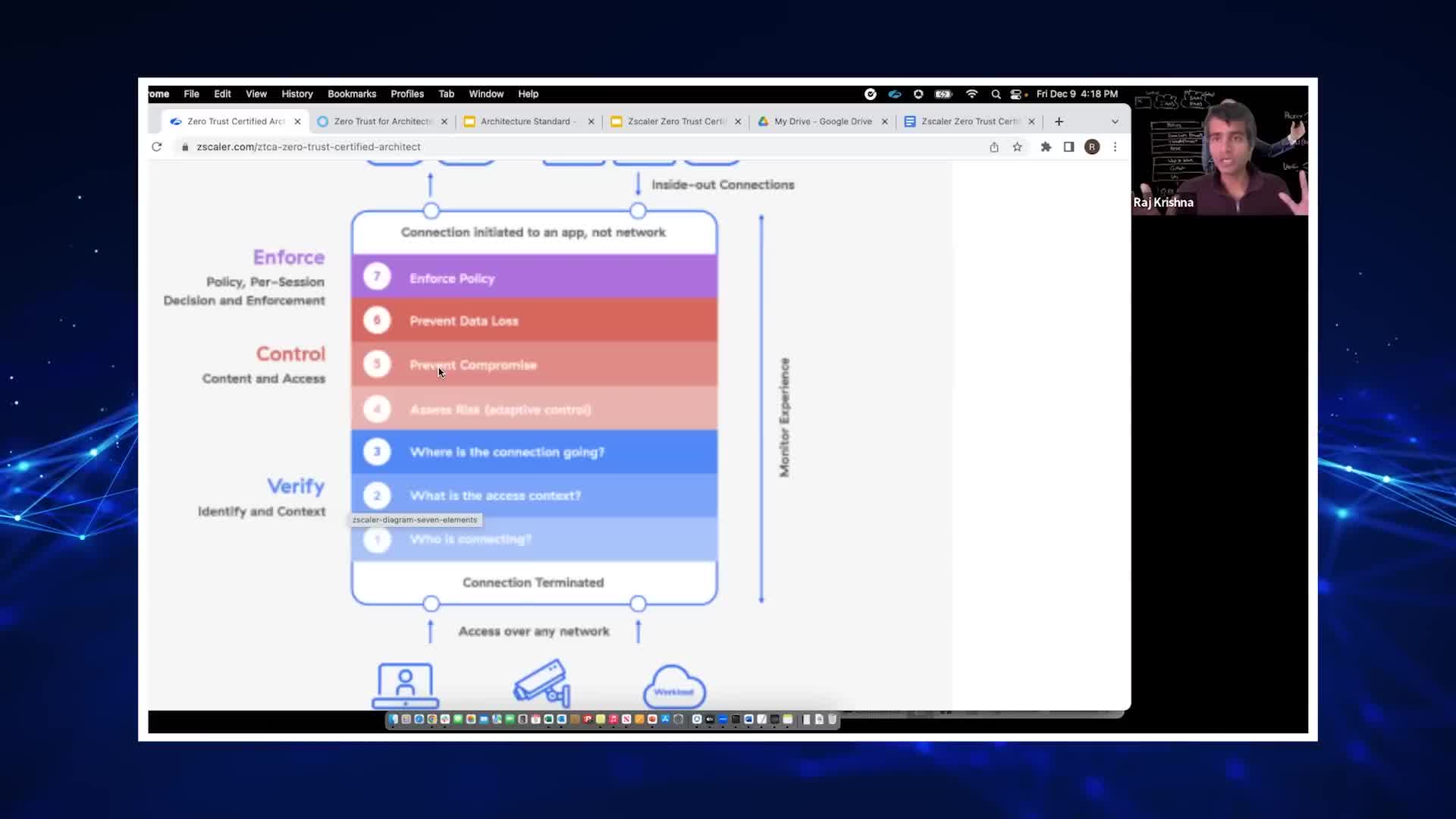
Information Security
What benefits do participants receive when completing Zscaler's Zero Trust Certification program?
Participants in Zscaler's Zero Trust Certification program receive several valuable benefits. Upon certification, they can post a LinkedIn badge and an encrypted URL similar to cloud certifications from AWS or GCP, providing professional validation. For a limited time, participants can use a special promo code to waive the $300 fee and gain full access to all program materials. Additionally, the first thousand people who complete the course will receive exclusive perks including a free T-shirt and a printed copy of the related book, making early participation particularly rewarding.
Watch clip answer (00:46m)What happens when organizations fail to implement cybersecurity recommendations after a breach?
As illustrated by Lee Kim's client example, organizations that experience a breach but fail to improve their cybersecurity measures often face repeated attacks. This particular client suffered a second breach just two weeks after the initial incident because they neglected to conduct a postmortem analysis, implement tabletop exercises to test defenses, or deploy necessary security tools. In healthcare especially, the stakes are exceptionally high since compromised patient data, unlike financial information, cannot be replaced or restored once exposed. Breached healthcare data, particularly sensitive information like genomic sequences, remains permanently vulnerable once compromised.
Watch clip answer (00:55m)What critical security failures did the FTC identify at GoDaddy that led to multiple breaches?
The FTC identified several fundamental security lapses at GoDaddy that contributed to multiple breaches between 2019-2022. Most notably, GoDaddy lacked basic multifactor authentication (MFA) for critical systems, which allowed attackers to gain access through a single compromised password in one incident that exposed 1.2 million WordPress customers' data. Other significant failures included improper software update management, insufficient security event logging, lack of network segmentation, poor asset tracking, and inadequate monitoring for threats. These gaps enabled attackers to install malware, steal source code, and access sensitive customer information including email addresses, admin passwords, database logins, and even SSL private keys - essentially providing complete access to websites and their data.
Watch clip answer (03:18m)How does AI impact cybersecurity?
AI is a double-edged sword in cybersecurity. On one hand, it empowers defenders with advanced tools that analyze massive datasets at unprecedented speeds, detect threats in real time, identify malicious code with high accuracy, and automate incident response for more efficient handling of potential threats. This allows security teams to be more proactive rather than reactive. On the other hand, AI is also a powerful tool for attackers, enabling them to create sophisticated malware capable of adapting and evolving to bypass security measures. AI-powered attacks can generate convincing phishing attempts that trick even cautious individuals and spread disinformation at alarming rates. This dual nature makes AI both revolutionary for defense while simultaneously creating new vulnerabilities organizations must address.
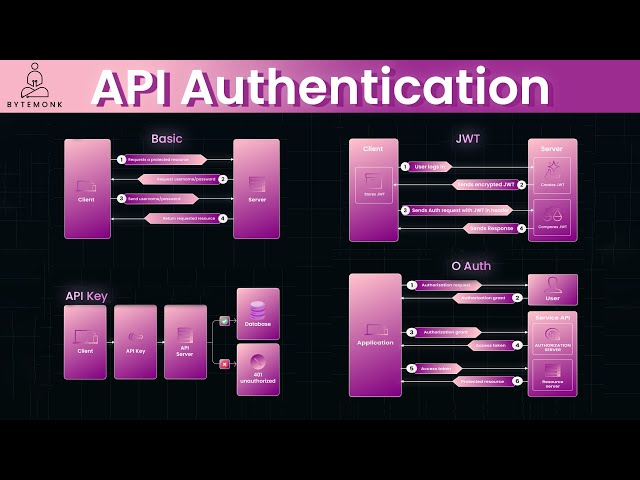
Watch clip answer (01:44m)What is JWT authentication and how does it work?
JWT (JSON Web Token) is a compact, stateless mechanism for API authentication. When a user logs in, the API server creates a digitally signed, encrypted token containing the user's identity. The client includes this JWT in every subsequent request for validation. The user's data isn't stored server-side, improving scalability. JWT is popular because it allows servers to issue tokens that clients use for future authentication without storing session data. The token contains signed user information that can't be tampered with, making it ideal for securing APIs in stateless environments.
Watch clip answer (01:34m)How can the healthcare system build resiliency against cybersecurity breaches like the one at Change Healthcare?
Healthcare systems need backup systems to ensure operational resilience against cybersecurity attacks. The recent Change Healthcare breach demonstrated that providers with alternative systems could shift to their backups without interruption, while those without backups suffered weeks of delayed payments, causing significant operational challenges, especially in rural areas. UnitedHealth's CEO Andrew Witty emphasizes the importance of creating a business model with built-in redundancy - a 'second rail' or pipeline that allows providers to maintain operations during technology failures. This approach requires working directly with healthcare providers to implement backup solutions that can activate immediately when primary systems are compromised, ensuring continuous patient care and payment processing.
Watch clip answer (01:44m)