Data Protection
Data protection is an essential concept in today’s digital landscape, encompassing strategies aimed at safeguarding sensitive data from unauthorized access, loss, or corruption. This multi-faceted discipline includes a range of practices and technologies, such as data encryption, backup solutions, and incident response plans, which ensure data integrity, availability, and compliance with various legal requirements. With tightening global regulations like the General Data Protection Regulation (GDPR) in Europe and the California Consumer Privacy Act (CCPA) in the United States, organizations are increasingly prioritizing robust data protection frameworks to avoid heavy penalties and maintain customer trust. The relevance of data protection is underscored by alarming statistics revealing that the average cost of a data breach reached millions, highlighting the financial and reputational stakes involved. Modern data protection practices not only focus on preventing breaches but also emphasize the importance of data management throughout its lifecycle—from collection to destruction—while ensuring compliance with evolving data privacy laws. As regulatory environments become more stringent and consumers demand increased transparency and control over their personal information, adopting effective data protection measures is no longer optional for organizations; it is a critical business necessity. In this context, understanding key elements of data privacy laws, such as data minimization and user consent requirements, as well as the tools and technologies that facilitate compliance is crucial for organizations operating in an increasingly complex and data-driven world.
What are the most hackable passwords according to recent findings?
According to a report released by Hostn IT Service Management company, many common passwords are extremely vulnerable to hacking. The report analyzes passwords based on how frequently they appear in data breaches, revealing which ones are most likely to be compromised. The analysis suggests that simple passwords like '123456' and 'password' (inferred from context) are among the most hackable options that users should avoid. The report emphasizes the importance of reevaluating password strength, as many people mistakenly believe their passwords are secure when they're actually easily compromised.
Watch clip answer (00:12m)How does one ensure that their password is safe and secure?
To ensure password safety, use complex passwords that are at least 20 characters long with a mix of uppercase and lowercase letters, numbers, and special symbols. This combination makes passwords significantly harder for hackers to crack through automated methods. Equally important is avoiding password reuse across multiple websites or services. When one account gets compromised, using the same password elsewhere puts all your other accounts at risk. Each unique service should have its own distinct password to maintain your overall digital security.
Watch clip answer (00:24m)What are the most common hackable passwords and why are they vulnerable?
According to Hostn IT's report, the top 10 most common and hackable passwords can be cracked in less than a second. Consecutive strings of numbers dominate these passwords, with '123456' being the most commonly used password. Other sequential combinations like '123', '1234', and '12345' also rank among the top 10 most common passwords. These simple numerical sequences are extremely vulnerable because hackers can easily predict and crack them using automated tools. The popularity of such basic passwords demonstrates how many users prioritize convenience over security, creating significant risks for their online accounts and personal information.
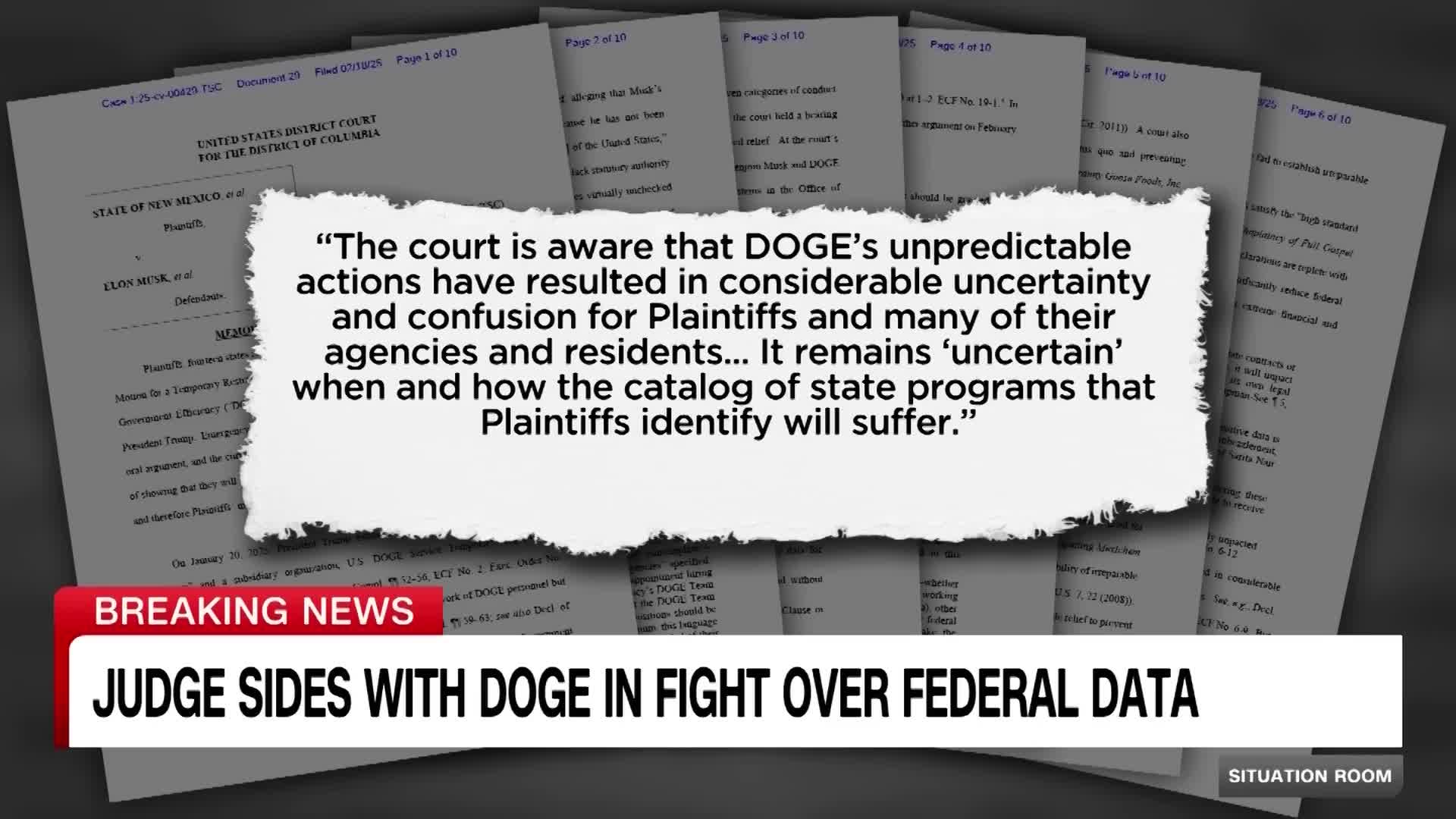
Watch clip answer (00:26m)What recent legal victories has the Department of Government Efficiency (Doge) achieved regarding access to federal data?
Doge has secured two significant legal victories regarding access to federal data. Most recently, Judge Randy Moss, an Obama-appointed judge in Washington, ruled that Doge would not be blocked from accessing data at the Department of Education. This follows a similar ruling by Judge Tanya Chutkan who allowed Elon Musk and Doge to access federal data despite concerns raised by Democratic state attorneys general. These consecutive wins represent important legal precedents for the Trump administration's Department of Government Efficiency as it seeks to gain access to government data systems.
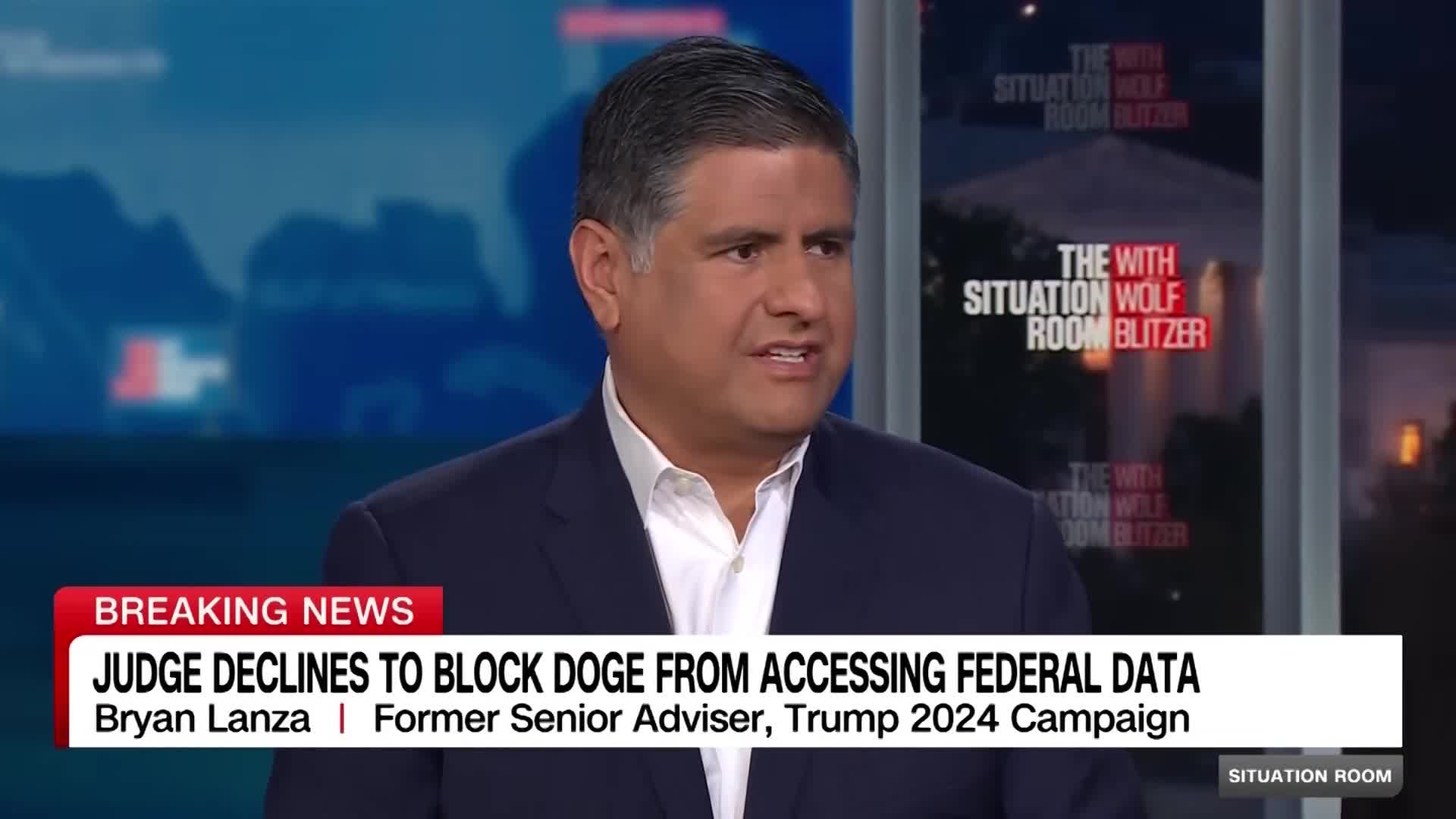
Watch clip answer (00:13m)What is Elon Musk's actual role in the Department of Government Efficiency (Doge)?
Contrary to the impression given by both Musk and Trump that Elon Musk is running Doge, Brian Lanza clarifies that Musk and his team serve as advisors to government agencies and the administration. They advise on identifying fraud, waste, and abuse within the system. In this advisory capacity, they sometimes require access to data, including sensitive information like Social Security numbers, to effectively identify issues such as duplicate entries. Their role is consultative rather than operational, focusing on providing guidance while maintaining appropriate boundaries regarding detailed involvement in government operations.
Watch clip answer (00:28m)Why are there concerns about Elon Musk accessing sensitive federal data?
The concerns stem from Musk lacking proper security clearance while gaining access to sensitive government information. Critics question what accessing this data has to do with cutting government waste or addressing everyday concerns like consumer prices. The speaker argues there's no transparency about what information is being accessed, who's accessing it, and for what purpose it's being used. The situation is characterized as potentially compromising Americans' sensitive data, with allegations that Trump is allowing Musk unrestricted access to government information without proper oversight.
Watch clip answer (00:47m)