Data Governance
Data governance is an essential framework that ensures the efficient management of data throughout its lifecycle, encompassing the establishment of policies, procedures, and standards to uphold data quality, security, and compliance with regulatory requirements. As organizations generate vast amounts of data, effective data governance becomes increasingly crucial for maintaining stakeholder trust and enabling data-driven decision-making. With a focus on defining decision rights and accountability for data-related processes, data governance highlights the strategic oversight needed to convert data into a valuable asset rather than a potential liability. Recently, businesses have witnessed a shift in the purpose of data governance from merely a compliance requirement to a strategic business driver. According to studies, a significant number of organizations are now prioritizing data democratization and accessibility, integrating governance into workflows, and using AI-driven tools to streamline operations. This evolution reflects an increased recognition that maintaining high-quality data is foundational not only for regulatory compliance but also for enhancing operational efficiency and fostering innovation. As a result, best practices in data governance increasingly involve comprehensive data quality management, clear role assignments, dynamic metadata utilization, and the implementation of adaptive governance frameworks that support agility in a fast-paced business landscape. Organizations that invest in robust data governance frameworks are better equipped to navigate the complexities of regulatory environments while maximizing the value extracted from their data.
What is Security Compliance?
Security compliance refers to following regulations, standards and guidelines set to protect sensitive information and data. It ensures that organizations implement necessary measures to safeguard data from unauthorized access or breaches, and is crucial in various industries to maintain data integrity and confidentiality. The process involves regular audits and assessments to ensure adherence to legal requirements and industry best practices. Non-compliance can result in severe consequences, including financial penalties and damage to an organization's reputation. By implementing proper security compliance measures, organizations demonstrate their commitment to protecting data security and privacy.
Watch clip answer (00:42m)What makes Deepseek's AI model development approach revolutionary compared to major competitors?
Deepseek, a Chinese startup, claims to have built AI models comparable to GPT-4 at significantly lower costs, spending only $5.6 million compared to the massive budgets of OpenAI, Google, and Meta. The revolutionary aspect lies in their ability to achieve high-quality output and reasoning depth without requiring enormous computational resources. Their success appears to be rooted in the quality of training data rather than just computational power. As Anantha explains, it's about 'garbage in, garbage out' - the model's performance strongly depends on input data quality. Deepseek likely leveraged high-quality, clean, structured data, possibly including outputs from existing models like ChatGPT, to train more efficient models that challenge the conventional wisdom that AI development requires massive budgets and resources.
Watch clip answer (01:49m)What is Elon Musk's role in the Department of Government Efficiency (Doge) and why does he need access to data?
Elon Musk and his team serve as advisors to government agencies and the administration, specifically focusing on identifying fraud, waste, and abuse within the system. Their advisory role is essential for pinpointing where government inefficiencies exist and recommending improvements. To effectively fulfill this function, they sometimes require access to data, including sensitive information like Social Security numbers. This access is necessary to ensure there are no duplicates or fraudulent activities occurring within government systems. Despite concerns about privacy, their data access is purposeful - aimed at improving government efficiency through targeted analysis of where wasteful spending occurs.
Watch clip answer (00:12m)What is Elon Musk's actual role in the Department of Government Efficiency (Doge)?
Contrary to the impression given by both Musk and Trump that Elon Musk is running Doge, Brian Lanza clarifies that Musk and his team serve as advisors to government agencies and the administration. They advise on identifying fraud, waste, and abuse within the system. In this advisory capacity, they sometimes require access to data, including sensitive information like Social Security numbers, to effectively identify issues such as duplicate entries. Their role is consultative rather than operational, focusing on providing guidance while maintaining appropriate boundaries regarding detailed involvement in government operations.
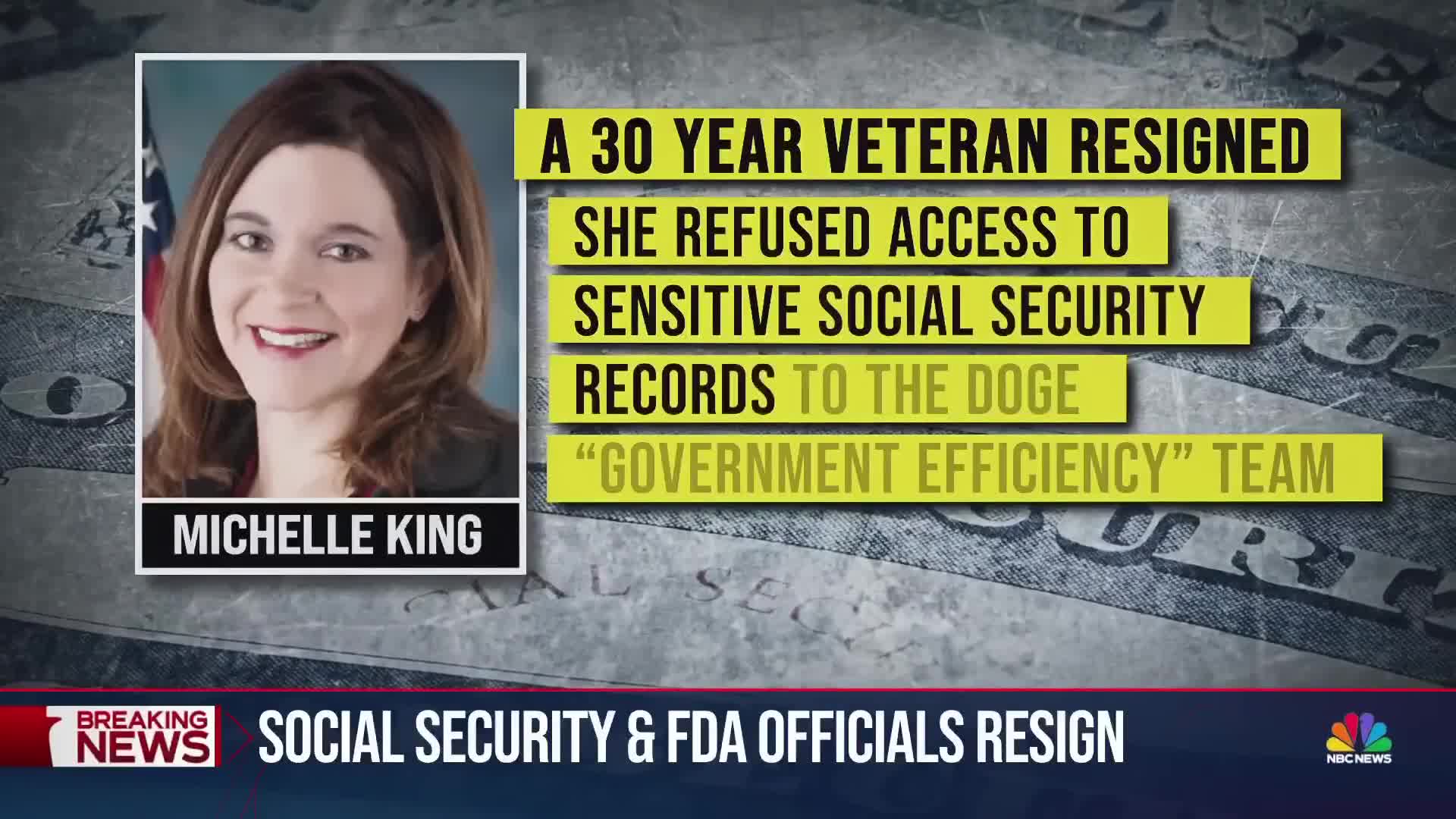
Watch clip answer (00:28m)Why did Acting Commissioner Michelle King resign from the Social Security Administration?
Michelle King, a 30-year veteran of the Social Security Administration, resigned after reportedly refusing to provide access to sensitive Social Security records containing citizens' financial and medical information to the DOGE Government Efficiency Team. The White House confirmed King's resignation and stated that the president is seeking the most qualified individuals rather than those who prioritize bureaucratic compliance. This resignation highlights tensions between government efficiency initiatives and concerns over sensitive data access in federal agencies.
Watch clip answer (00:22m)What legal protections exist if your personal information is leaked by the federal government?
There are specific laws requiring the government to treat personal data with utmost care, privacy, and certain restrictions. If such data leaks occur, individuals have legal recourse through civil suits and potentially even criminal charges if the leaks were done negligently or in an irresponsible manner. While these protective laws exist, their enforcement mechanisms remain to be fully tested, which explains why many people feel nervous about government handling of sensitive information. The legal framework provides a foundation for accountability, though the practical application of these protections in real-world scenarios is still evolving.
Watch clip answer (00:44m)