Cybersecurity
Cybersecurity refers to the practice of protecting systems, networks, and data from cyber threats, which have become increasingly prevalent and sophisticated in our digital age. As cyberattacks rise, with numerous reports highlighting a surge in incidents such as ransomware and phishing campaigns, effective cybersecurity has become crucial for both individuals and organizations. The landscape is evolving rapidly, marked by the integration of artificial intelligence (AI) in both attacks and defenses, making it essential for entities to adopt proactive and layered cybersecurity solutions. Recent trends indicate that navigating the complexities of cybersecurity now requires an emphasis on innovative frameworks such as Zero Trust Architectures, which prioritize continuous verification and micro-segmentation. Moreover, organizations are grappling with a significant skills gap in the cybersecurity workforce, leaving many unprepared for the latest threats that exploit vulnerabilities in interconnected systems. With the escalating cost of data breaches and the proliferation of AI-driven threats, implementing comprehensive data breach prevention strategies has never been more critical. By focusing on robust network security measures, regular security assessments, and adherence to compliance standards, organizations can enhance their cybersecurity posture in an increasingly hostile environment.
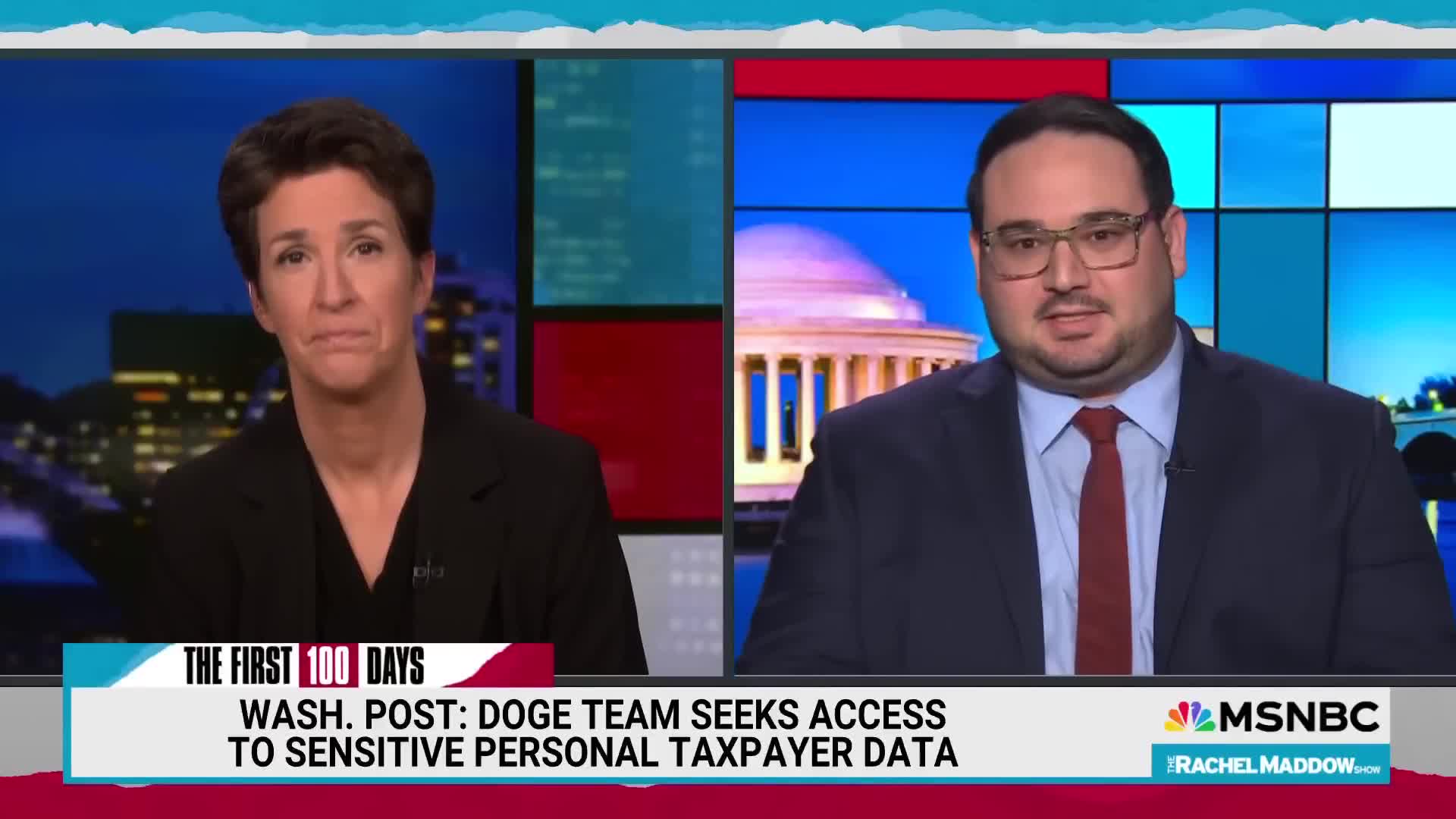
What are the main privacy concerns regarding Elon Musk's DOGE group accessing IRS records?
The primary concern is that this non-governmental entity would have access to highly sensitive personal data, including Social Security numbers and banking information that Americans provide when filing taxes. Privacy advocates worry about what DOGE might do with this information or the potential security risks if the entity were hacked. While third-party auditing of government systems is standard practice, the unprecedented nature of someone like Elon Musk accessing these records has raised significant alarm. Several groups are now suing to block DOGE from accessing these private IRS records due to data security implications.
Watch clip answer (00:56m)How have Bitcoin scammers evolved their tactics to make their schemes more believable?
Bitcoin scammers have significantly sophisticated their approach by personalizing their threats with victims' real information. Rather than generic messages, they now use victims' actual names and addresses in their extortion attempts, making the scams more frightening and credible. The clip describes how scammers claim to have installed spyware and recorded compromising activities, threatening to release this content to friends and social media unless a Bitcoin payment (around $2,000) is made. These tactics create fear by demonstrating they possess personal information, preventing victims from contacting authorities, and establishing urgency to coerce immediate payment.
Watch clip answer (00:34m)What sophisticated phone scam did Joe Rogan experience and how did it unfold?
Joe Rogan fell victim to an elaborate phone scam where the caller posed as a sheriff from Travis County with a legitimate local number (512 area code). The scammer claimed Rogan was required to be an expert witness in a court case but failed to appear, allegedly breaking federal law. With police radio chatter playing in the background for authenticity, the scammer told Rogan he needed to pay a fine to avoid being arrested. The scammer maintained control by insisting Rogan couldn't call his lawyer and had a "do not hang up order." The scam became obvious when the caller requested Rogan obtain a "coupon" to send money. Despite the red flags, the scam was so convincing that Rogan was deceived for 15 minutes before realizing it was fraudulent.
Watch clip answer (01:24m)What is fueling the rise in cyber attacks in India and how serious is the threat?
The Dark Web is a key driver behind India's unprecedented surge in cyber attacks, which are surpassing global averages. Nearly 56.8% of Dark Web content is linked to illegal activities including financial fraud and cybercrime, creating an underground economy that facilitates data breaches and identity theft. This growing threat significantly impacts businesses, with reports showing approximately 543 million digital assets linked to Fortune 1000 employees available for sale. Ransomware-related breaches have doubled annually over the past two years, severely affecting financial stability and corporate reputation. Despite India contributing 26% of the Dark Web's user base, awareness remains low, making Indian businesses particularly vulnerable targets for cybercriminals.
Watch clip answer (04:08m)What is fueling the rise of cyber attacks in India?
Cyber attacks in India are increasing at a rate significantly higher than the global average, with the Dark Web playing a central role in this surge. Around 20% of cybercrimes in India are directly linked to Dark Web activities, where an underground economy thrives on stolen data and ransomware attacks. This digital threat landscape particularly impacts critical sectors, businesses, and individuals as India undergoes rapid digitization. The increasing prevalence of digital transactions has created new vulnerabilities that cybercriminals are actively exploiting, raising serious concerns about whether India is adequately prepared to counter these sophisticated cyber threats.
Watch clip answer (00:15m)What controversy is surrounding the White House and the IRS regarding access to sensitive tax information?
According to the Washington Post, the White House is pressuring the IRS to grant access to sensitive tax information to a 25-year-old software engineer associated with Elon Musk. This individual has reportedly been trying to delete their online history of amplifying white supremacist content and praising Holocaust deniers. Concurrently, NBC News has confirmed that the acting head of the Social Security Administration has resigned following a conflict with Musk's team over access to sensitive data in their system. These developments raise significant concerns about the security of confidential taxpayer information and the appropriate boundaries of government data access.
Watch clip answer (00:43m)