Cybersecurity
Cybersecurity refers to the practice of protecting systems, networks, and data from cyber threats, which have become increasingly prevalent and sophisticated in our digital age. As cyberattacks rise, with numerous reports highlighting a surge in incidents such as ransomware and phishing campaigns, effective cybersecurity has become crucial for both individuals and organizations. The landscape is evolving rapidly, marked by the integration of artificial intelligence (AI) in both attacks and defenses, making it essential for entities to adopt proactive and layered cybersecurity solutions. Recent trends indicate that navigating the complexities of cybersecurity now requires an emphasis on innovative frameworks such as Zero Trust Architectures, which prioritize continuous verification and micro-segmentation. Moreover, organizations are grappling with a significant skills gap in the cybersecurity workforce, leaving many unprepared for the latest threats that exploit vulnerabilities in interconnected systems. With the escalating cost of data breaches and the proliferation of AI-driven threats, implementing comprehensive data breach prevention strategies has never been more critical. By focusing on robust network security measures, regular security assessments, and adherence to compliance standards, organizations can enhance their cybersecurity posture in an increasingly hostile environment.
How does one ensure that their password is safe and secure?
To ensure password safety, use complex passwords that are at least 20 characters long with a mix of uppercase and lowercase letters, numbers, and special symbols. This combination makes passwords significantly harder for hackers to crack through automated methods. Equally important is avoiding password reuse across multiple websites or services. When one account gets compromised, using the same password elsewhere puts all your other accounts at risk. Each unique service should have its own distinct password to maintain your overall digital security.
Watch clip answer (00:24m)What are the most common hackable passwords and why are they vulnerable?
According to Hostn IT's report, the top 10 most common and hackable passwords can be cracked in less than a second. Consecutive strings of numbers dominate these passwords, with '123456' being the most commonly used password. Other sequential combinations like '123', '1234', and '12345' also rank among the top 10 most common passwords. These simple numerical sequences are extremely vulnerable because hackers can easily predict and crack them using automated tools. The popularity of such basic passwords demonstrates how many users prioritize convenience over security, creating significant risks for their online accounts and personal information.
Watch clip answer (00:26m)Why did the top official at the Social Security Administration resign?
The top official at the Social Security Administration resigned after DOGE employees attempted unauthorized access to sensitive personnel data. This confidential information included bank account details, Social Security numbers, and medical information of individuals who had applied for disability benefits, affecting millions of Americans. The official oversaw the system responsible for disbursing Social Security payments to approximately 70 million Americans. The breach attempt targeted highly sensitive personal and financial information, which ultimately led to the official's resignation from their position.
Watch clip answer (00:47m)What was Alan Fillion sentenced for and what was his punishment?
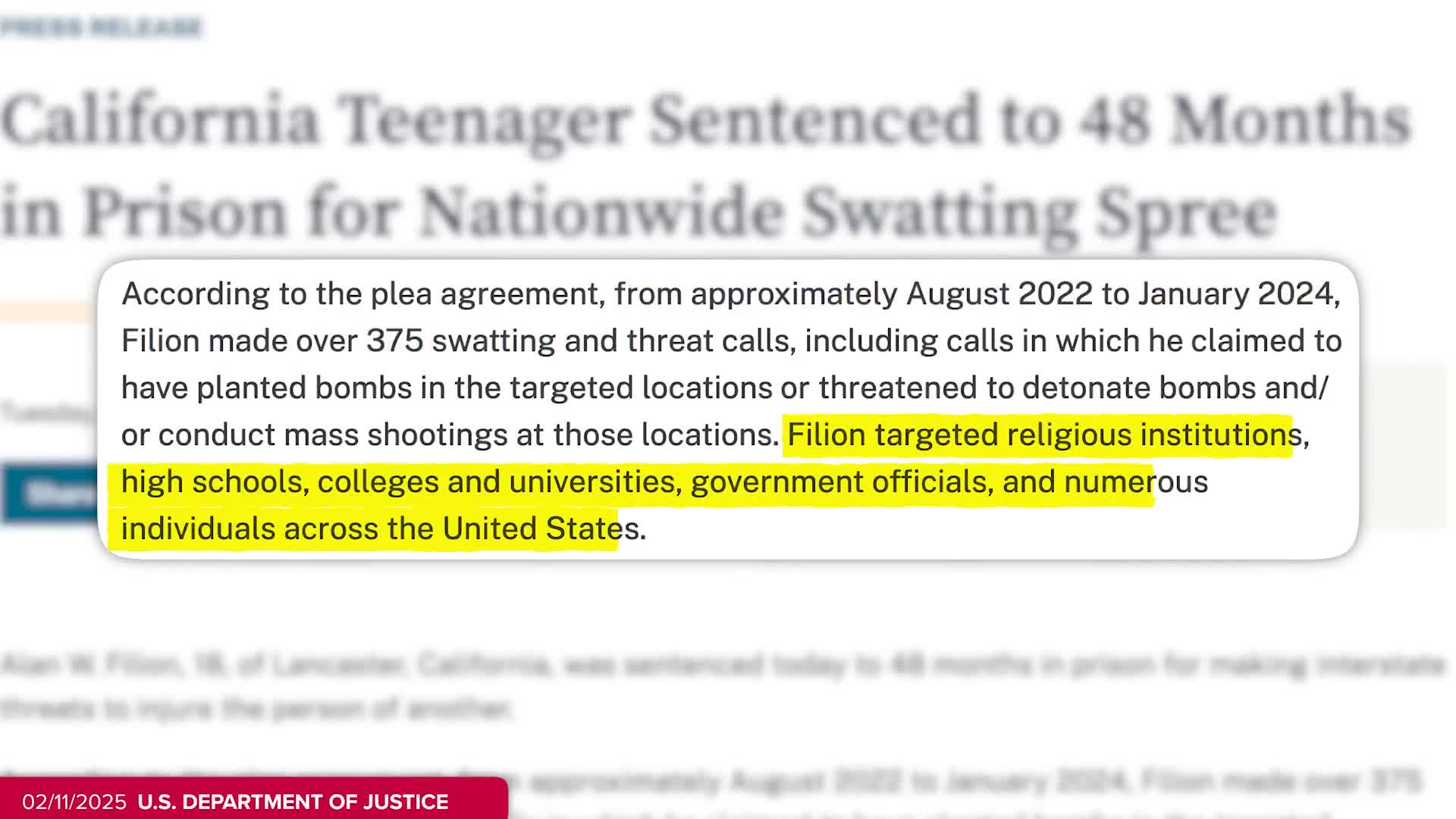
Alan Fillion was sentenced to four years in federal prison for orchestrating a swatting campaign. As described in the clip, Fillion was responsible for over 375 swatting calls, including those with fake gunfire sounds and threats made in the name of Satan. These dangerous actions put countless lives at risk, as swatting involves making false emergency calls to provoke an armed police response to an innocent person's address. Fillion's case highlights the serious legal consequences now being imposed for this form of online harassment, which has become an increasing concern in digital culture.
Watch clip answer (00:16m)How did Alan Fillion's swatting activities evolve from a personal activity to a criminal enterprise?
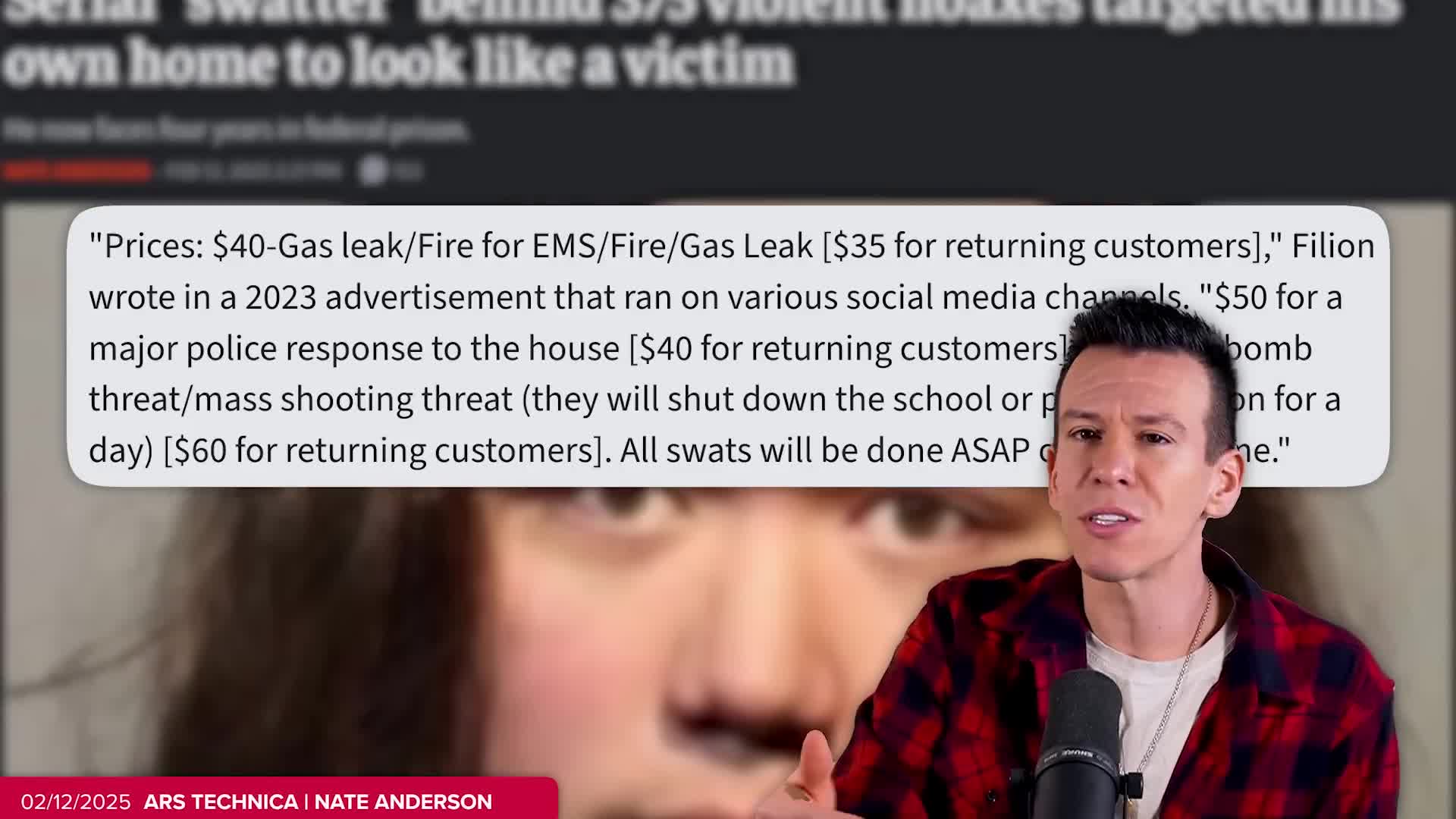
According to the transcript, Fillion's swatting activities began as what he described as a 'power drip' - likely referring to a feeling of control or influence. However, he quickly transformed this harmful behavior into a profit-making 'side hustle.' Fillion commercialized his criminal activities by advertising his swatting 'services' across social media platforms with specific price points. The transcript reveals he offered various types of emergency hoaxes, including gas leak and fire reports that would trigger EMS response, charging approximately $40 per incident. This evolution from personal gratification to monetized criminal enterprise demonstrates the calculated nature of Fillion's extensive swatting campaign that ultimately led to his four-year prison sentence.
Watch clip answer (00:11m)What measures does Pokimane take to protect herself from online security threats?
Pokimane employs extensive security measures to protect herself from online threats, including hiring a dedicated online security team. This professional approach comes with significant financial costs, highlighting the serious investment required for content creators to maintain their privacy and safety in today's digital landscape. As online threats continue to increase, Pokimane has established robust protocols to combat potential doxxing and harassment, demonstrating the pressing need for safety measures where social media presence and personal privacy intersect.
Watch clip answer (00:07m)