Cybersecurity
Cybersecurity refers to the practice of protecting systems, networks, and data from cyber threats, which have become increasingly prevalent and sophisticated in our digital age. As cyberattacks rise, with numerous reports highlighting a surge in incidents such as ransomware and phishing campaigns, effective cybersecurity has become crucial for both individuals and organizations. The landscape is evolving rapidly, marked by the integration of artificial intelligence (AI) in both attacks and defenses, making it essential for entities to adopt proactive and layered cybersecurity solutions. Recent trends indicate that navigating the complexities of cybersecurity now requires an emphasis on innovative frameworks such as Zero Trust Architectures, which prioritize continuous verification and micro-segmentation. Moreover, organizations are grappling with a significant skills gap in the cybersecurity workforce, leaving many unprepared for the latest threats that exploit vulnerabilities in interconnected systems. With the escalating cost of data breaches and the proliferation of AI-driven threats, implementing comprehensive data breach prevention strategies has never been more critical. By focusing on robust network security measures, regular security assessments, and adherence to compliance standards, organizations can enhance their cybersecurity posture in an increasingly hostile environment.
What critical security failures did the FTC identify at GoDaddy that led to multiple breaches?
The FTC identified several fundamental security lapses at GoDaddy that contributed to multiple breaches between 2019-2022. Most notably, GoDaddy lacked basic multifactor authentication (MFA) for critical systems, which allowed attackers to gain access through a single compromised password in one incident that exposed 1.2 million WordPress customers' data. Other significant failures included improper software update management, insufficient security event logging, lack of network segmentation, poor asset tracking, and inadequate monitoring for threats. These gaps enabled attackers to install malware, steal source code, and access sensitive customer information including email addresses, admin passwords, database logins, and even SSL private keys - essentially providing complete access to websites and their data.
Watch clip answer (03:18m)How does AI impact cybersecurity?
AI is a double-edged sword in cybersecurity. On one hand, it empowers defenders with advanced tools that analyze massive datasets at unprecedented speeds, detect threats in real time, identify malicious code with high accuracy, and automate incident response for more efficient handling of potential threats. This allows security teams to be more proactive rather than reactive. On the other hand, AI is also a powerful tool for attackers, enabling them to create sophisticated malware capable of adapting and evolving to bypass security measures. AI-powered attacks can generate convincing phishing attempts that trick even cautious individuals and spread disinformation at alarming rates. This dual nature makes AI both revolutionary for defense while simultaneously creating new vulnerabilities organizations must address.
Watch clip answer (01:44m)What vulnerability exists in the OpenPGP JavaScript crypto library?
The OpenPGP JavaScript crypto library contains a significant vulnerability where it fails to correctly verify message signatures, making them susceptible to spoofing. This flaw compromises the integrity of encrypted communications by enabling potential manipulation of messages processed through this library. This vulnerability directly endangers the security of end-to-end encrypted systems that rely on this popular library. Security researcher Johannes Ulrich emphasizes that developers working with such systems should ensure they update this library promptly to protect the integrity of sensitive communications and prevent potential exploitation of this signature verification weakness.
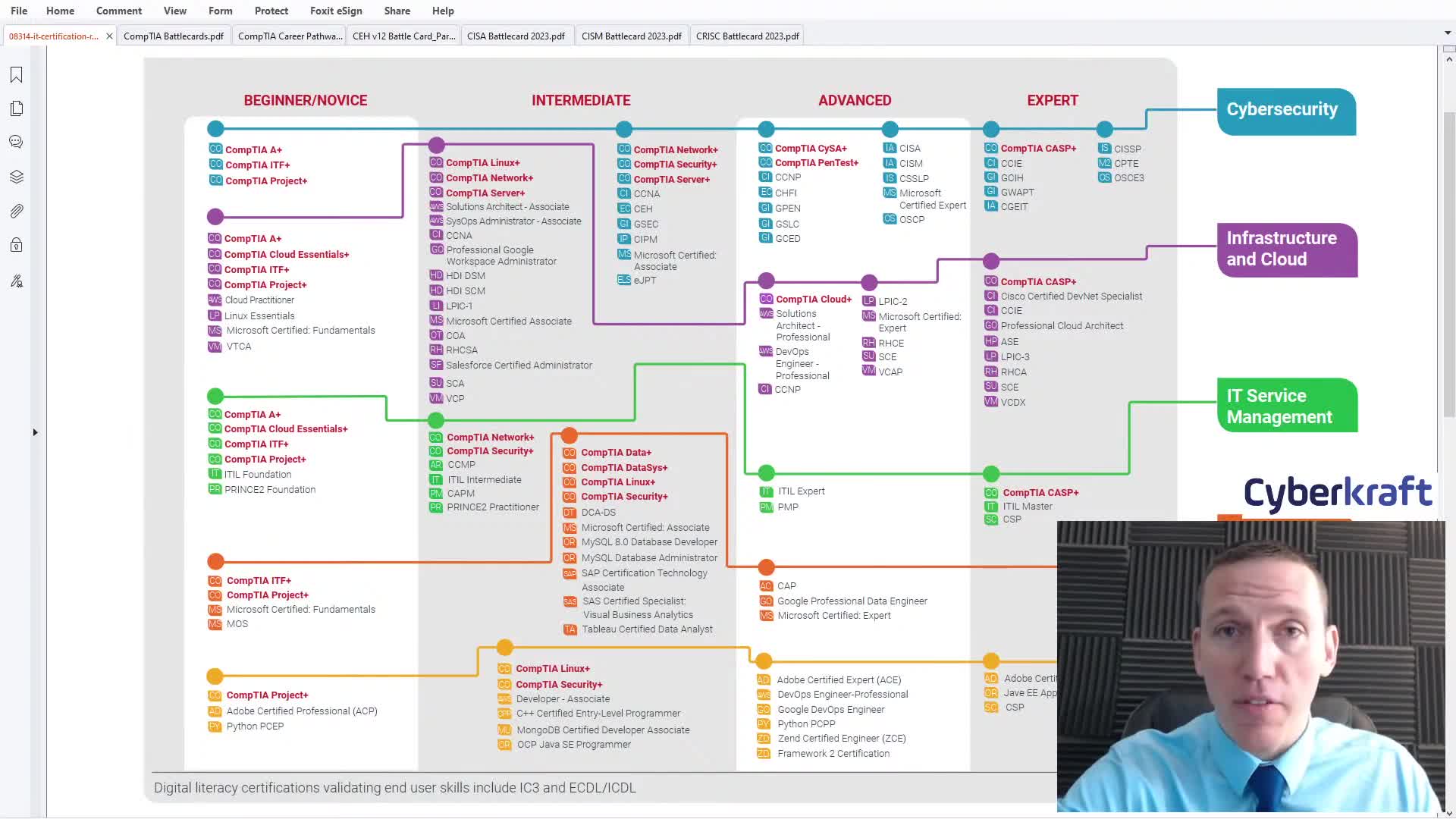
Watch clip answer (00:43m)What cybersecurity certifications should I pursue for different career paths in cybersecurity?
For blue team roles in security operations centers (SOC), the CompTIA CySA+ (Cybersecurity Analyst) certification is recommended as it teaches operations center skills, incident management, automation, and working with security information management tools. It's specifically designed for SOC analysts and frequently appears in job descriptions. For red team or penetration testing roles, the Certified Ethical Hacker (CEH) from EC Council is highly recommended. The CEH provides comprehensive training in real-world hacking tools and methodologies, teaching students about attack techniques, malware creation, penetration testing, and privilege escalation. CEH is more recognized in job descriptions and typically associated with higher salaries compared to alternatives like CompTIA PenTest+.
Watch clip answer (03:24m)How can the healthcare system build resiliency against cybersecurity breaches like the one at Change Healthcare?
Healthcare systems need backup systems to ensure operational resilience against cybersecurity attacks. The recent Change Healthcare breach demonstrated that providers with alternative systems could shift to their backups without interruption, while those without backups suffered weeks of delayed payments, causing significant operational challenges, especially in rural areas. UnitedHealth's CEO Andrew Witty emphasizes the importance of creating a business model with built-in redundancy - a 'second rail' or pipeline that allows providers to maintain operations during technology failures. This approach requires working directly with healthcare providers to implement backup solutions that can activate immediately when primary systems are compromised, ensuring continuous patient care and payment processing.
Watch clip answer (01:44m)How has Reddit's stance on AI companies been hypocritical?
Reddit has positioned itself as a victim of AI companies, claiming these companies scrape content without permission, while simultaneously negotiating massive licensing deals and selling users' posts, comments, and metadata to corporations like OpenAI for model training without user consent or transparency. This hypocrisy reveals that Reddit's outrage isn't about ethics or protecting their community, but about losing control over who profits from user data exploitation. While publicly criticizing AI companies, Reddit executives have willingly turned the platform into a commercial data farm when it served their financial interests, betraying their self-portrayal as defenders of privacy.
Watch clip answer (08:25m)