Cyber Threats
In today's interconnected world, cyber threats represent one of the most pressing challenges for individuals and organizations alike. These threats, which encompass a wide array of malicious activities—including malware attacks, phishing schemes, and ransomware incidents—are increasingly sophisticated and prevalent. As cybercriminals continue to refine their tactics, understanding the landscape of cybersecurity threats becomes essential for effective defense and risk mitigation. Recent reports indicate that attacks such as Distributed Denial of Service (DDoS) and Man-in-the-Middle (MitM) have grown in complexity, often exploiting vulnerabilities in encrypted communications and overwhelming networks to disrupt services. Ransomware, particularly Ransomware-as-a-Service (RaaS), has emerged as a dominant force in cybercrime, threatening critical infrastructure across various sectors. Phishing attacks, a foundational element of social engineering, leverage advanced tactics—such as voice phishing and tailored business email compromises—to manipulate victims into divulging sensitive information. With the escalating risks associated with these cyber threats, effective strategies now emphasize adaptive defenses that integrate artificial intelligence for enhanced anomaly detection and identity protection. Implementing a Zero Trust architecture, which promotes continuous authentication and micro-segmentation of networks, has also become a core strategy for organizations striving to protect their digital assets in this evolving threat landscape. Given that cybersecurity threats are constantly evolving, proactive measures encompassing threat intelligence, regular security assessments, and robust incident response plans are critical for safeguarding against the multitude of risks present in today's digital environment.
How did Alan Fillion's swatting activities evolve from a personal activity to a criminal enterprise?
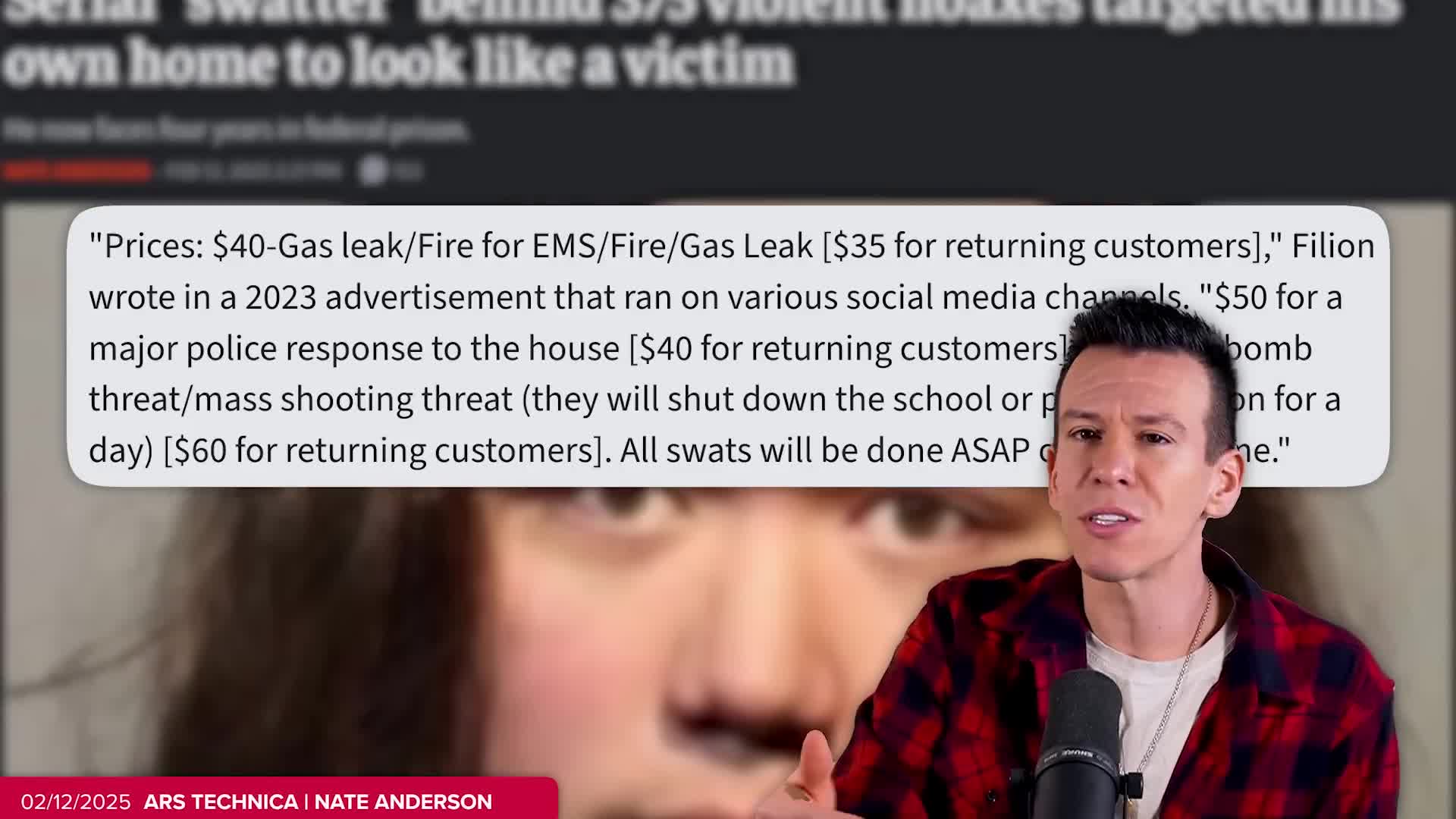
According to the transcript, Fillion's swatting activities began as what he described as a 'power drip' - likely referring to a feeling of control or influence. However, he quickly transformed this harmful behavior into a profit-making 'side hustle.' Fillion commercialized his criminal activities by advertising his swatting 'services' across social media platforms with specific price points. The transcript reveals he offered various types of emergency hoaxes, including gas leak and fire reports that would trigger EMS response, charging approximately $40 per incident. This evolution from personal gratification to monetized criminal enterprise demonstrates the calculated nature of Fillion's extensive swatting campaign that ultimately led to his four-year prison sentence.
Watch clip answer (00:11m)How have Bitcoin scammers evolved their tactics to make their schemes more believable?
Bitcoin scammers have significantly sophisticated their approach by personalizing their threats with victims' real information. Rather than generic messages, they now use victims' actual names and addresses in their extortion attempts, making the scams more frightening and credible. The clip describes how scammers claim to have installed spyware and recorded compromising activities, threatening to release this content to friends and social media unless a Bitcoin payment (around $2,000) is made. These tactics create fear by demonstrating they possess personal information, preventing victims from contacting authorities, and establishing urgency to coerce immediate payment.
Watch clip answer (00:34m)What sophisticated phone scam did Joe Rogan experience and how did it unfold?
Joe Rogan fell victim to an elaborate phone scam where the caller posed as a sheriff from Travis County with a legitimate local number (512 area code). The scammer claimed Rogan was required to be an expert witness in a court case but failed to appear, allegedly breaking federal law. With police radio chatter playing in the background for authenticity, the scammer told Rogan he needed to pay a fine to avoid being arrested. The scammer maintained control by insisting Rogan couldn't call his lawyer and had a "do not hang up order." The scam became obvious when the caller requested Rogan obtain a "coupon" to send money. Despite the red flags, the scam was so convincing that Rogan was deceived for 15 minutes before realizing it was fraudulent.
Watch clip answer (01:24m)Is it true that AI has the potential to destroy our society and potentially end humanity?
While this concern isn't entirely unfounded, it represents an ongoing debate in AI development. The conversation indicates that artificial intelligence does pose some legitimate risks to social order that warrant serious consideration. Several AI experts and researchers have expressed concerns about advanced AI systems potentially disrupting societal structures if developed without proper safeguards. The discussion acknowledges these concerns while suggesting that responsible governance and understanding AI's capabilities are essential for mitigating these risks. Current dialogue around AI regulation aims to balance harnessing its benefits while preventing harmful outcomes.
Watch clip answer (00:24m)What is fueling the rise in cyber attacks in India and how serious is the threat?
The Dark Web is a key driver behind India's unprecedented surge in cyber attacks, which are surpassing global averages. Nearly 56.8% of Dark Web content is linked to illegal activities including financial fraud and cybercrime, creating an underground economy that facilitates data breaches and identity theft. This growing threat significantly impacts businesses, with reports showing approximately 543 million digital assets linked to Fortune 1000 employees available for sale. Ransomware-related breaches have doubled annually over the past two years, severely affecting financial stability and corporate reputation. Despite India contributing 26% of the Dark Web's user base, awareness remains low, making Indian businesses particularly vulnerable targets for cybercriminals.
Watch clip answer (04:08m)What is fueling the rise of cyber attacks in India?
Cyber attacks in India are increasing at a rate significantly higher than the global average, with the Dark Web playing a central role in this surge. Around 20% of cybercrimes in India are directly linked to Dark Web activities, where an underground economy thrives on stolen data and ransomware attacks. This digital threat landscape particularly impacts critical sectors, businesses, and individuals as India undergoes rapid digitization. The increasing prevalence of digital transactions has created new vulnerabilities that cybercriminals are actively exploiting, raising serious concerns about whether India is adequately prepared to counter these sophisticated cyber threats.
Watch clip answer (00:15m)