Cyber Threats
In today's interconnected world, cyber threats represent one of the most pressing challenges for individuals and organizations alike. These threats, which encompass a wide array of malicious activities—including malware attacks, phishing schemes, and ransomware incidents—are increasingly sophisticated and prevalent. As cybercriminals continue to refine their tactics, understanding the landscape of cybersecurity threats becomes essential for effective defense and risk mitigation. Recent reports indicate that attacks such as Distributed Denial of Service (DDoS) and Man-in-the-Middle (MitM) have grown in complexity, often exploiting vulnerabilities in encrypted communications and overwhelming networks to disrupt services. Ransomware, particularly Ransomware-as-a-Service (RaaS), has emerged as a dominant force in cybercrime, threatening critical infrastructure across various sectors. Phishing attacks, a foundational element of social engineering, leverage advanced tactics—such as voice phishing and tailored business email compromises—to manipulate victims into divulging sensitive information. With the escalating risks associated with these cyber threats, effective strategies now emphasize adaptive defenses that integrate artificial intelligence for enhanced anomaly detection and identity protection. Implementing a Zero Trust architecture, which promotes continuous authentication and micro-segmentation of networks, has also become a core strategy for organizations striving to protect their digital assets in this evolving threat landscape. Given that cybersecurity threats are constantly evolving, proactive measures encompassing threat intelligence, regular security assessments, and robust incident response plans are critical for safeguarding against the multitude of risks present in today's digital environment.
How has cybercrime changed during the pandemic?
During the pandemic, cybercrime has increased disproportionately compared to pre-2019 levels. This significant rise is attributed to inadequate home security systems and organizations lacking proper secure architecture like firewalls. According to experts, the number of digital misdemeanor events and the quantum of losses have substantially increased as people worked remotely. Many victims fell prey to these crimes due to negligence, mistakes, or simply being targets of wrongdoing, highlighting how the pandemic exposed critical vulnerabilities in existing cybersecurity infrastructures.
Watch clip answer (01:33m)What are the key recommendations for creating secure passwords?
According to Hostn IT Service Management, users should avoid common password setups like '123456' or simply 'password' as these are easily hackable. Instead, create long, complex passwords that combine uppercase and lowercase letters, numbers, and special characters to significantly enhance online security. Additionally, it's crucial to avoid reusing passwords across multiple sites, as a breach on one platform can compromise all your accounts. Implementing these password management practices helps protect both personal and professional data from unauthorized access in today's digital landscape.
Watch clip answer (00:03m)How does one ensure that their password is safe and secure?
To ensure password safety and security, users should create complex passwords that are at least 20 characters long. These passwords should incorporate a mix of uppercase and lowercase letters, numbers, and special characters to maximize security against potential hackers. Additionally, it's crucial to avoid reusing passwords across different platforms, as a breach on one site could compromise multiple accounts. Using unique, lengthy, and complex combinations significantly reduces the risk of falling victim to common password hacking techniques.
Watch clip answer (00:09m)What are the most hackable passwords according to recent findings?
According to a report released by Hostn IT Service Management company, many common passwords are extremely vulnerable to hacking. The report analyzes passwords based on how frequently they appear in data breaches, revealing which ones are most likely to be compromised. The analysis suggests that simple passwords like '123456' and 'password' (inferred from context) are among the most hackable options that users should avoid. The report emphasizes the importance of reevaluating password strength, as many people mistakenly believe their passwords are secure when they're actually easily compromised.
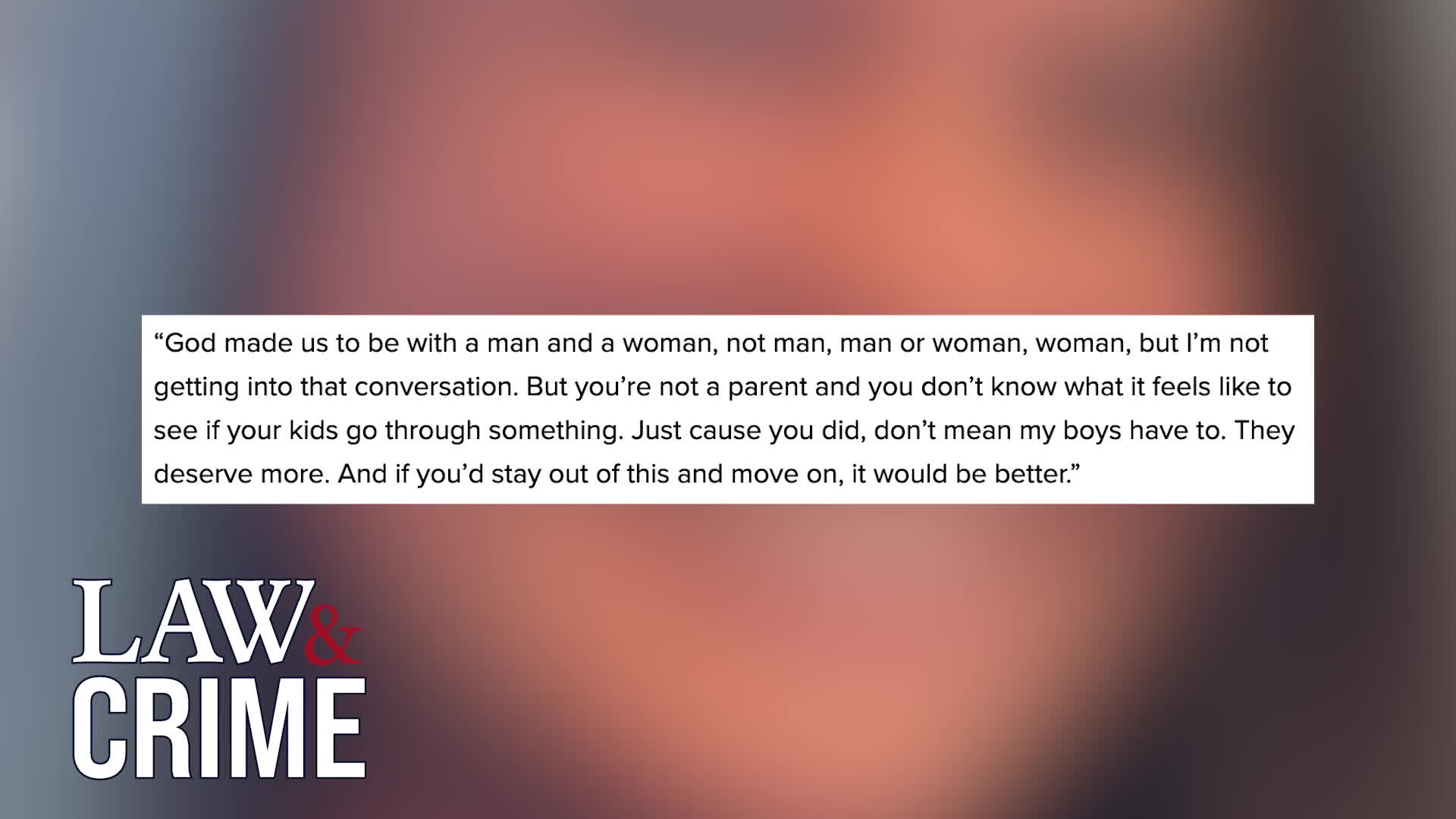
Watch clip answer (00:12m)What motive led Sammy Schaefer to allegedly orchestrate the murder of Portia Rowland?
According to prosecutors at a pretrial hearing, Sammy Schaefer was motivated by jealousy over Rowland dating his estranged wife during what was described as a contentious divorce. Evidence suggests Schaefer made direct threats to Rowland in the weeks before her murder. He allegedly sent messages saying "I wish you would let go of her and let my family heal together again for my sons," followed by another message reading "God made us to be with a man and a woman." These communications reveal Schaefer's apparent desperation to reunite his family and his resentment toward Rowland for her relationship with his estranged wife.
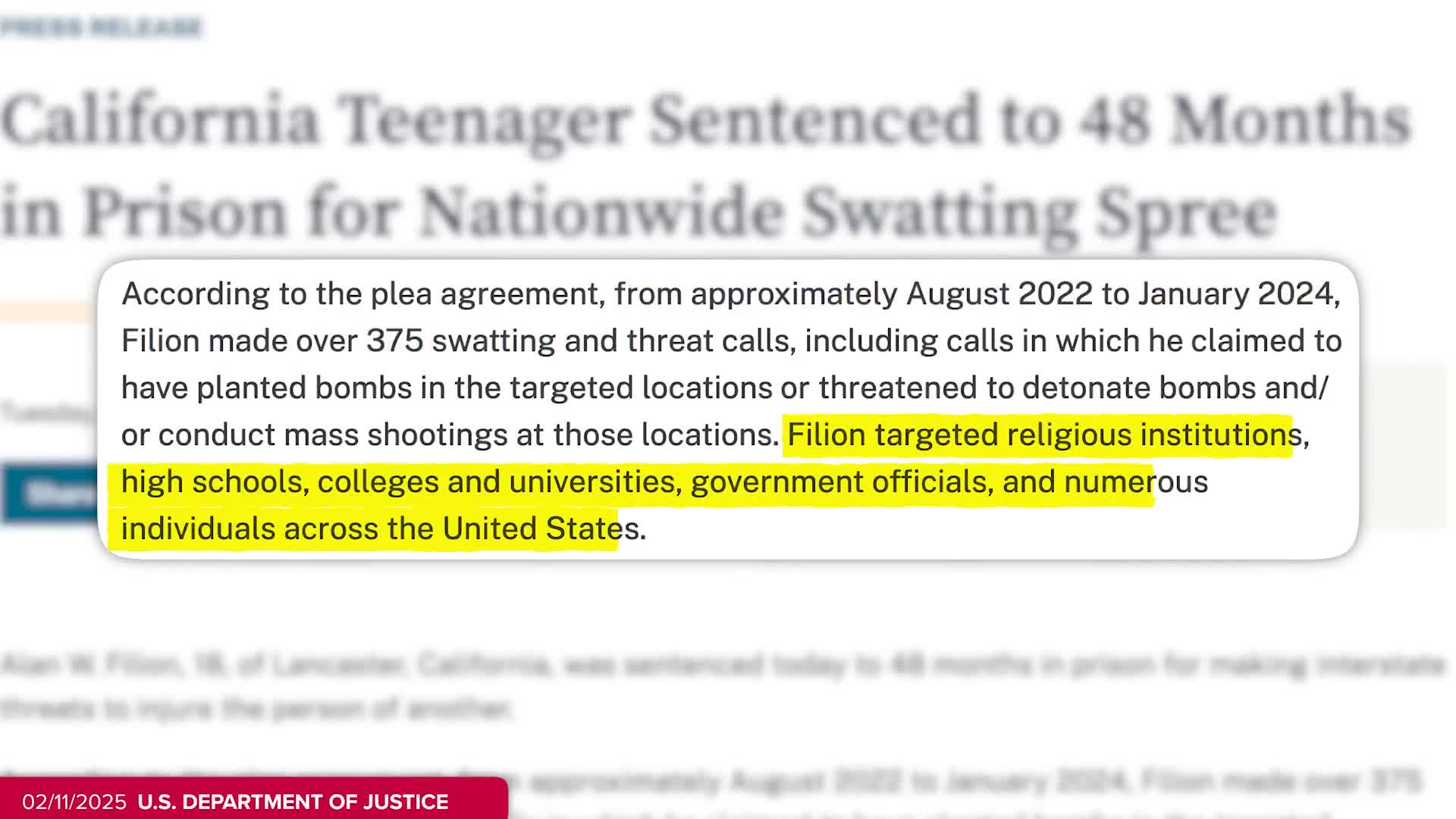
Watch clip answer (00:37m)What was Alan Fillion sentenced for and what was his punishment?
Alan Fillion was sentenced to four years in federal prison for orchestrating a swatting campaign. As described in the clip, Fillion was responsible for over 375 swatting calls, including those with fake gunfire sounds and threats made in the name of Satan. These dangerous actions put countless lives at risk, as swatting involves making false emergency calls to provoke an armed police response to an innocent person's address. Fillion's case highlights the serious legal consequences now being imposed for this form of online harassment, which has become an increasing concern in digital culture.
Watch clip answer (00:16m)