Data Breaches
Data breaches refer to incidents where unauthorized individuals or entities gain access to sensitive or confidential information, resulting in significant ramifications for businesses, individuals, and society at large. As the digital landscape expands and interconnected systems proliferate, the prevalence and complexity of data breaches continue to rise, affecting millions and often leading to severe financial losses. It is estimated that the average cost of a data breach has recently reached approximately $4.44 million globally, with the U.S. reporting average breach costs as high as $10.22 million. Notably, sectors like healthcare and financial services are particularly vulnerable, facing higher costs due to the sensitive nature of the data involved. The increasing reliance on cloud infrastructures has also contributed to the surge in data breaches. Recently, findings indicate that around 72% of breaches involved data stored in cloud environments, highlighting the critical importance of robust security measures in these platforms. Common causes of data breaches include human error—identified as a contributing factor in 95% of incidents—social engineering, and vulnerabilities within third-party vendor systems. Adopting a comprehensive data breach prevention strategy, including effective breach response plans and employee training, is essential for mitigating risk. As technology evolves, understanding the threat landscape surrounding data breaches emphasizes the need for proactive cybersecurity measures across all organizations.
What sensitive military information did the ex-soldier leak to a foreign agency?
According to China's Ministry of State Security, the ex-soldier shared photos and videos containing highly classified military intelligence through social media channels. The leaked information included sensitive details about troop deployment locations, weapon configurations, and comprehensive information about military barracks positioned near border areas. The ministry stated this disclosure occurred on Tuesday, with the sensitive materials being transmitted directly to a foreign espionage agency, constituting a serious breach of national security.
Watch clip answer (00:17m)What sensitive military information did the ex-soldier share with a foreign espionage agency?
According to China's Ministry of State Security, the ex-soldier transmitted photos and videos containing highly sensitive military intelligence to a foreign espionage agency through social media platforms. The shared information included details about troop deployment locations, weapon configurations, and specific information about military barracks positioned near border areas. This security breach represents a significant compromise of national defense information, particularly concerning military assets in strategically sensitive border regions. The disclosure was officially reported by China's Ministry of State Security in a statement released on Tuesday.
Watch clip answer (00:19m)What are the concerns about Doge accessing Social Security data?
Former Social Security Commissioner Martin O'Malley expresses uncertainty about what exactly Doge wants access to within Social Security data. When asked about his understanding of what Doge is seeking, O'Malley candidly stated, 'I'm not sure. I don't even think they know what they want exactly.' This uncertainty raises significant concerns about potential misuse of sensitive personal information, especially by untrained staff. As the former commissioner under President Biden, O'Malley's hesitation reflects broader worries about protecting the integrity of an agency that maintains low overhead and efficient operations, contradicting claims of widespread fraud in the system.
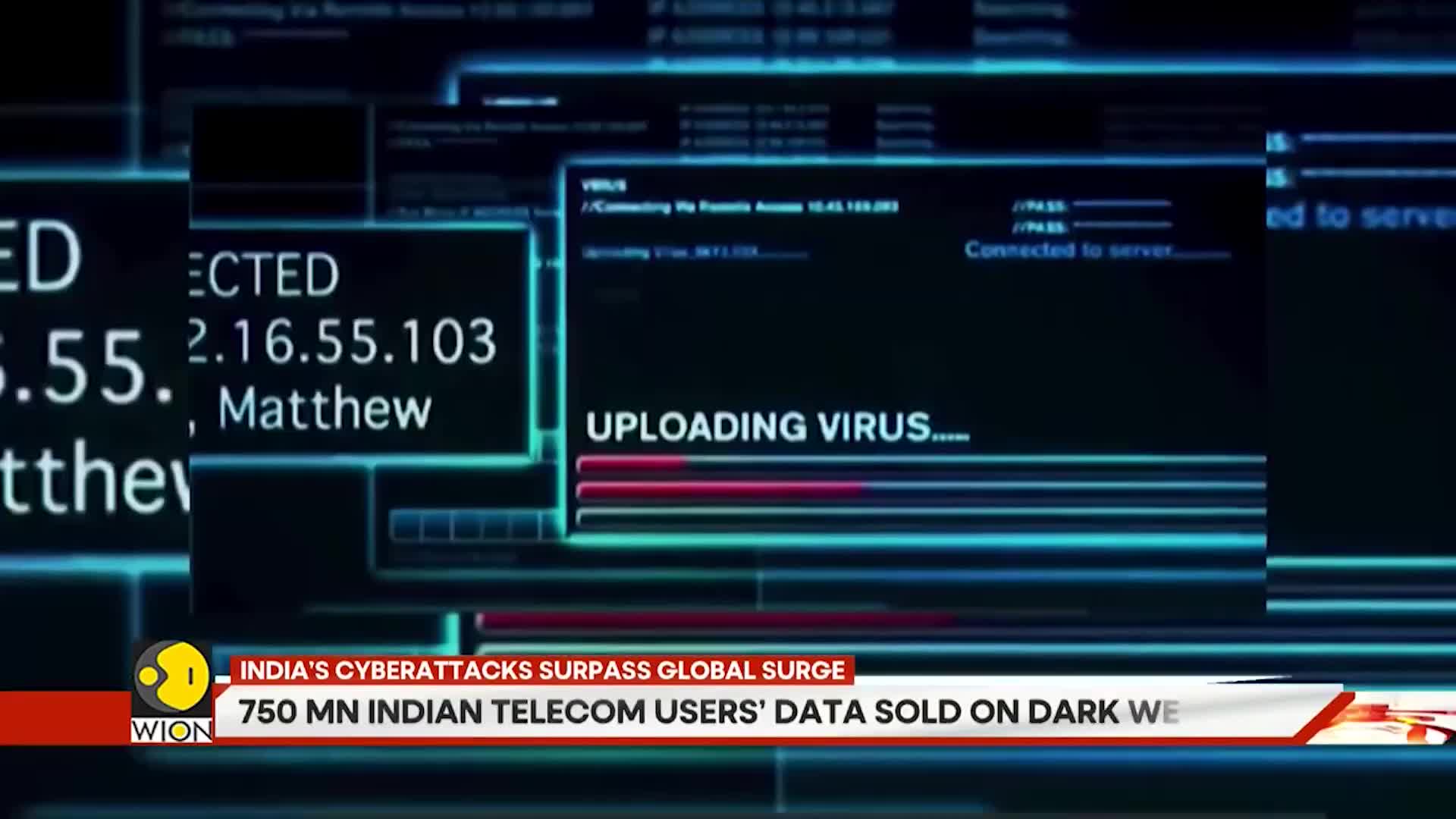
Watch clip answer (00:12m)What is fueling the rise in cyber attacks in India and how serious is the threat?
The Dark Web is a key driver behind India's unprecedented surge in cyber attacks, which are surpassing global averages. Nearly 56.8% of Dark Web content is linked to illegal activities including financial fraud and cybercrime, creating an underground economy that facilitates data breaches and identity theft. This growing threat significantly impacts businesses, with reports showing approximately 543 million digital assets linked to Fortune 1000 employees available for sale. Ransomware-related breaches have doubled annually over the past two years, severely affecting financial stability and corporate reputation. Despite India contributing 26% of the Dark Web's user base, awareness remains low, making Indian businesses particularly vulnerable targets for cybercriminals.
Watch clip answer (04:08m)What is fueling the rise of cyber attacks in India?
Cyber attacks in India are increasing at a rate significantly higher than the global average, with the Dark Web playing a central role in this surge. Around 20% of cybercrimes in India are directly linked to Dark Web activities, where an underground economy thrives on stolen data and ransomware attacks. This digital threat landscape particularly impacts critical sectors, businesses, and individuals as India undergoes rapid digitization. The increasing prevalence of digital transactions has created new vulnerabilities that cybercriminals are actively exploiting, raising serious concerns about whether India is adequately prepared to counter these sophisticated cyber threats.
Watch clip answer (00:15m)How much money could be saved by addressing fraud in the U.S. tax and entitlement systems?
According to the discussion between Jesse Watters and Greg Gutfeld, over a 10-year normal budget window, the government could potentially save over a trillion dollars by clamping down on massive fraud in tax and entitlement systems. The fraud involves criminals using fake identities to steal billions in taxpayer benefits. The exact amount is difficult to determine without full access to the data, but the scale of the problem is significant enough that addressing it could recover substantial taxpayer funds that are currently being stolen through organized fraud schemes targeting government benefit programs and tax systems.
Watch clip answer (00:20m)